Sports brand Puma infected with advanced malware

by Sansec Forensics Team
Published in Threat Research − April 29, 2019
On April 25th, sports brand Puma Australia got infected with the most sophisticated payment skimmer to date.

After the NBA Hawks got skimmed last week, this time Puma's Australian customers are cannon fodder for Magecart thieves. Anyone who ordered a pair of sneakers online, had their name, address and credit card sent to a server registered in Odessa, Ukraine.
This skimmer is the most advanced we have seen so far: it features polymorphic properties and supports over 50 different payment gateways. In a seperate blog we explain why this particular skimmer is an amazing feat of engineering.
Malware in the Puma store
On April 25th, Sansec's global Magecart Detection Network identified suspicious code on the checkout page of au.puma.com (screenshot). This obfuscated code embeds an extra script file called jqueres.com/js/lib/jquery-1.10.2.min.js, which in turn activates a keystroke sniffer.
Behavioral analysis using a bait order confirmed the leakage of private data:
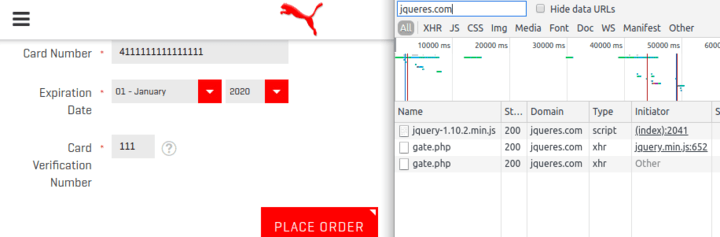
The data that gets sent to Ukraine is the encoded contents of the checkout form:
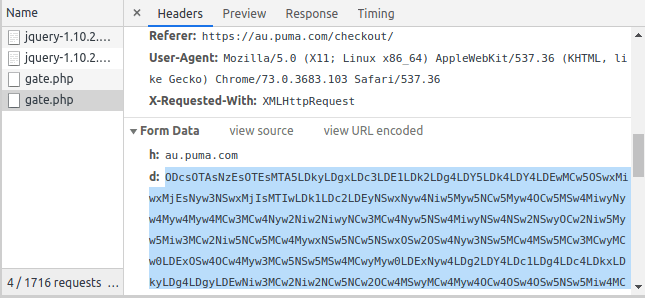
We have notified Puma of the breach using the given contact address onlinestore-au@puma.com, but have not heard back. At the time of writing, the skimmer is still present & active.
How did attackers gain access
Puma Australia uses Magento 2.2. A critical security patch was released in March, but the store appears patched as of today. Either the attackers gained access before the patch was applied, or attackers used insecure third-party components to gain access to the core of the shop system. Our previous research has uncovered a range of popular vectors: database management tools, marketing plugins and connected accounting software are in the top-3.
How to prevent or mitigate a Magecart attack?
New attack methods are literally discovered every week. Whenever a new attack pattern emerges, it usually takes 6 to 12 hours before stores across the globe are getting exploited. Because the timeframe is so small, you need an automated solution to identify and prevent attacks. Our eComscan threat and vulnerability monitor does just that. It is optimized for Magento and is the best protection that exist for merchants today.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
