Adobe patches critical Magento admin takeover via menu injection

by Sansec Forensics Team
Published in Threat Research − June 12, 2025
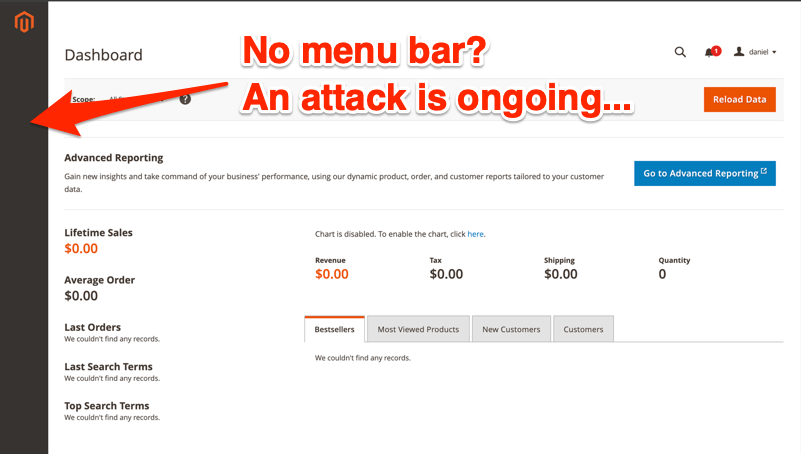
A new attack on Adobe Commerce may break the menu bar for admin users. If your menu bar is missing, someone is stealing your session via CVE-2025-47110.
Adobe has just released several security fixes for its Commerce (Magento) platform and one of them is critical (CVE-2025-47110). Adobe urges merchants to patch within 72 hours (highest priority).
Sansec was able to simulate a successful attack, and it is likely that cyber criminals will follow suit. Surprisingly, Adobe’s Cloud infrastructure has not yet enabled WAF protection against this vulnerability. We strongly recommend that merchants use active defenses, such as Sansec Shield, to block exploit attempts immediately, buying time for a no-stress upgrade.
Who’s at risk?
The following Magento and Adobe Commerce versions are vulnerable:
2.4.8
2.4.7-p5 and earlier
2.4.6-p10 and earlier
2.4.5-p12 and earlier
2.4.4-p13 and earlier
How does the attack work?
To make threat actors none the wiser we won’t disclose specific details. However, in general we can say that the attack builds upon last year’s CosmicSting attack and requires multiple attack stages:
- Use cache poisoning & stored XSS to replace the backend menu bar with malicious code
- Wait for an admin user to use the backend
- Take control of the admin session
- The menu bar reverts to its original state
An admin session effectively grants access to customer data, payment flows and code execution.
This attack will temporarily break the dashboard menu bar for admin users, which is clearly an indicator for an ongoing attack. However, staff may consider it a “fluke” if the menu works again after a minute or so, and not escalate it.
Sansec also found other admin blocks vulnerable to cache poisoning, such as the footer. While future attacks on these blocks can't be ruled out, they are less trivial to exploit.
Mitigation steps
Sansec Shield blocks this attack out of the box and Sansec eComscan has been updated with detection heuristics.
Not protected by Sansec yet? Use coupon STOREPROTECT to get our Advanced or Enterprise protection one month free of charge. Get yourself some peace of mind and upgrade on your own schedule.
As general mitigation, we recommend to rotate your secret crypt key if you haven’t done so after implementing the original CosmicSting patch APSB24-40.
See also
Adobes bulletin APSB25-50 (multiple fixes) and their isolated patch for CVE-2025-47110.
Shoutout to Julian Nuß of integer_net for an insightful discussion.
Credits to blaklis for discovering CVE-2025-47110.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
