Merchants struggle with MageCart reinfections

by Sansec Forensics Team
Published in Threat Research − November 12, 2018
1 in 5 compromised merchants get reinfected, average skimming operation lasts 13 days
MageCart, the notorious actors behind massive online card skimming, has been busy. And so have we: our crawlers are continuously tracking the raging battle between card thieves and merchants. It seems that the latter are on the losing end: in October, we counted the 40,000th hijacked store since 2015. And in the last 3 months alone, we counted 5,400 unique online stores that got a skimmer added to their checkout pages.
20% reinfection rate, counter measures fail
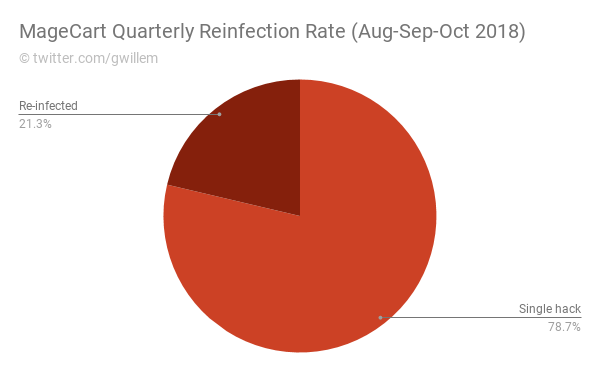
In the last quarter, 1 out of 5 breached stores were infected (and cleaned) multiple times, some even up to 18 times. This shows that counter measures taken by merchants and their contracted security firms often fail. There are multiple reasons for this. First, MageCart operatives are getting more sophisticated in hiding their presence and ensuring future access. Once an operative gains access to a merchant's server, it is common to litter the site with backdoors and rogue admin accounts. Second, they use reinfection mechanisms such as database triggers and hidden periodic tasks to reinstate their payload. Third, they use obfuscation techniques to make their presence indistinguishable from legitimate code. Fourth, it is more and more common for MageCart actors to utilize unpublished security exploits (aka 0days). Researching these requires a significant investment. All in all, it takes some very keen eyes and a lot of effort to clean all traces of a breach.
Black hats are faster than white hats
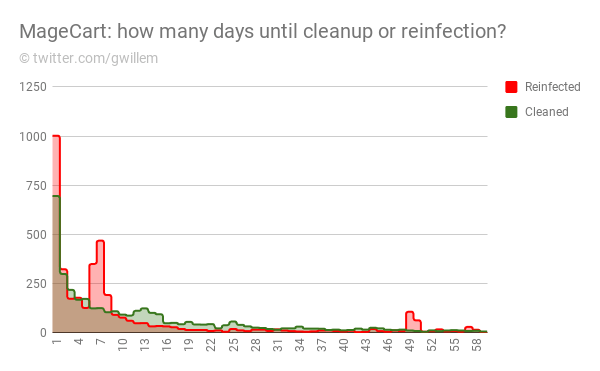
Here is a histogram of the number of days it takes merchants after a MageCart breach to clean up, and how many days between cleanup and a subsequent reinfection. Conclusion: skimmers persist on average for 12.7 days, while on average we saw reinfections occur within 10.5 days. The eCommerce industry is one step behind here.
Cleaned during the week, hacked in the weekend
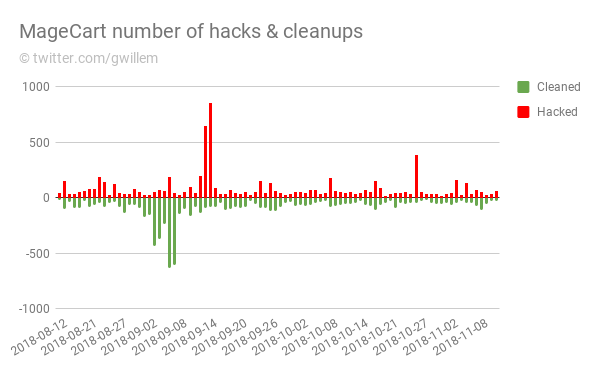
The red lines are newly identified infections, the green ones are cleanups. You can see that merchants and their security firms work mostly during the week, while the black hats, unsurprisingly, do not stick to office hours.
Conclusion
MageCart operations have become more professional while expanding methodologies and changing tactics. Merchants need to step up their efforts in protecting their reputation and the privacy of their customers.
Read more
In this article
What is Magecart?
Also known as digital skimming, this crime has surged since 2015. Criminals steal card data during online shopping. Who are behind these notorious hacks, how does it work, and how have Magecart attacks evolved over time?
About MagecartScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more