An OpenCart/Magento hacking dashboard

by Sansec Forensics Team
Published in Threat Research − April 07, 2017
This post shows how sophisticated Magento hacking operations have become nowadays.
While investigating a bruteforced Magento store, we noticed that the hacker logged in using a curious referrer site:
"GET /rss/catalog/notifystock/ HTTP/1.1" 200 5676 "http://194.87.232.147:777/"
The site at http://194.87.232.147:777/ shows:
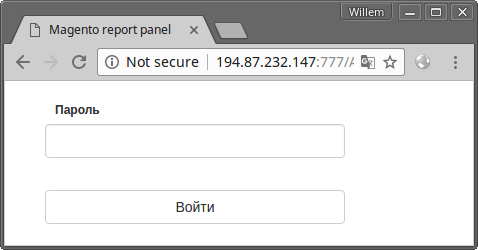
A "Magento report panel" asks for a Пароль (password). In the page source (beautified JS here) are some clues about its password protected functionality:
$.post("/home/getServers", function(n) {
$.post("/home/GetCountGoodLastDay", function(n) {
$.post("/home/GetCountServerLastDay", function(n) {
$.post("/home/GetCountSuccessLastDay", function(n) {
$.post("/home/ChangeMarkState", {
$.post("/home/ChangeComment", {
$.post("/home/getCount", {
$.post("/home/ChangeShell", {
$.post("/home/ChangeReservedLogins", {
Apparently somebody has built a sophisticated dashboard to manage bruteforce Magento hacking operations. It appears to show the daily progress on hacked Magento stores and it has a GUI method to mark found servers as "success". Also, it can be used to log in to the backend of hacked stores.
We checked our forensic notes of previous cases and found that this dashboard was used in at least one other case. Sysadmins, check your server logs.
Update April 11th: Super-sleuth Len Lorijn noted that an Opencart Report Panel(http://194.87.232.147:999/Account/Login?ReturnUrl=%2f) is running on the same server. This signifies that e-commerce hackers are platform agnostic. If there's money flowing through it, it's worth hacking.
Read more
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
