ConnectPOS leaked Github secrets for years
Sansec discovered that ConnectPOS has been showing their Github credentials on their site for 4 years. This would enable attackers to slip malicious code into each of the thousands of ConnectPOS retail installations. Sansec recommends to verify integrity of installed code.
Sansec researchers discovered that ConnectPOS, a popular Point of Sale solution, had been exposing a GitHub Personal Access Token (PAT) in their public installation instructions for over four years. The token had full repo access rights, meaning anyone who found it could push malicious code to ConnectPOS repositories.
What happened?
ConnectPOS publishes installation guides on their website. In September 2021, when they migrated from GitLab deploy tokens to GitHub PAT authentication, they included an access token in their public documentation to allow customers to download modules. However, the token was configured with full repo scope instead of read-only access, granting anyone who found it complete control over the repositories. This token remained exposed until we reported it on January 6th, 2026.
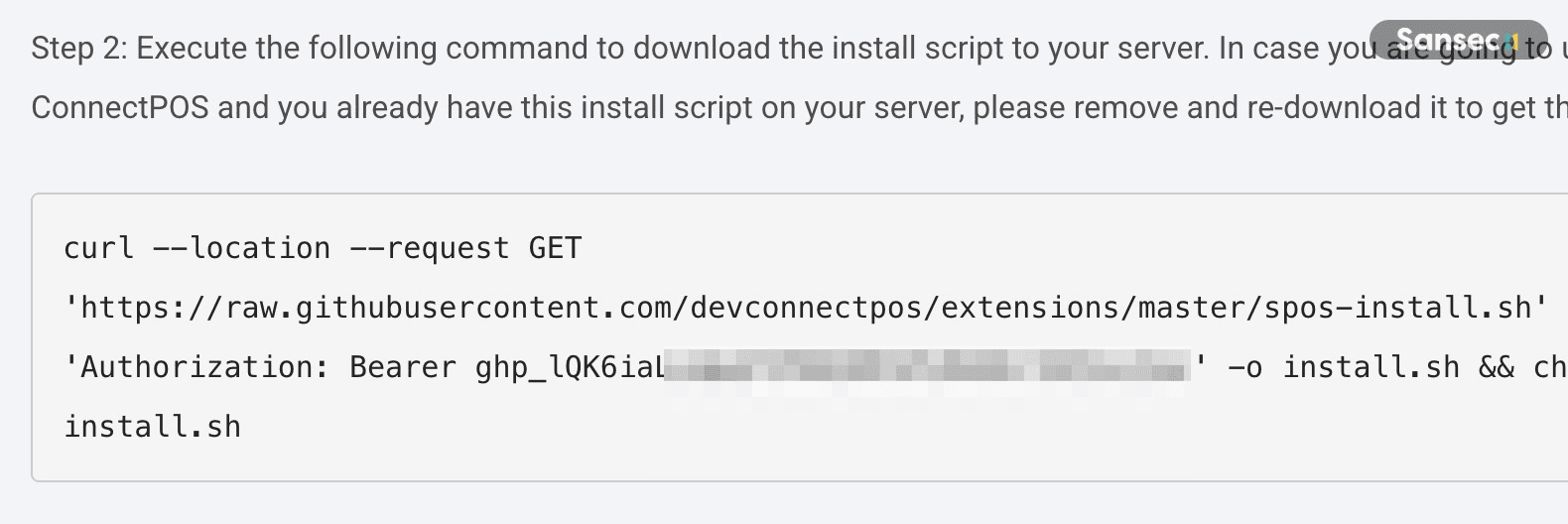
The token granted full administrative access to 59 repositories, covering everything from payment processing to inventory management:
devconnectpos/connectpos-module-aw-giftcard
devconnectpos/connectpos-module-boostmyshop
devconnectpos/connectpos-module-catalog
devconnectpos/connectpos-module-configuration
devconnectpos/connectpos-module-core
devconnectpos/connectpos-module-customer
devconnectpos/connectpos-module-giftcard
devconnectpos/connectpos-module-giftcard-integration
devconnectpos/connectpos-module-inventory
devconnectpos/connectpos-module-marketing
devconnectpos/connectpos-module-payment
devconnectpos/connectpos-module-quotation
devconnectpos/connectpos-module-quote
devconnectpos/connectpos-module-report
devconnectpos/connectpos-module-reward-points
devconnectpos/connectpos-module-sales
devconnectpos/connectpos-module-shipping
devconnectpos/connectpos-module-store-credit
devconnectpos/connectpos-module-store-pickup
devconnectpos/connectpos-module-webhook
devconnectpos/connectpos-package
devconnectpos/connectpos-woocommerce
devconnectpos/extensions
devconnectpos/m2-rest-api
devconnectpos/m23-rest-api
devconnectpos/module-adyen
devconnectpos/module-category
devconnectpos/module-core
devconnectpos/module-custom-sale
devconnectpos/module-customer
devconnectpos/module-customization
devconnectpos/module-discount-per-item
devconnectpos/module-discount-whole-order
devconnectpos/module-electronic-journal
devconnectpos/module-email
devconnectpos/module-eway
devconnectpos/module-integrate
devconnectpos/module-payment
devconnectpos/module-payment-express
devconnectpos/module-performance
devconnectpos/module-product
devconnectpos/module-pwa
devconnectpos/module-pwa-banner
devconnectpos/module-pwa-keyword
devconnectpos/module-pwa-qrcode
devconnectpos/module-refund-without-receipt
devconnectpos/module-report
devconnectpos/module-sales
devconnectpos/module-setting
devconnectpos/module-shell
devconnectpos/module-shift
devconnectpos/module-shipping
devconnectpos/module-store
devconnectpos/module-stripe
devconnectpos/module-tax
devconnectpos/module-tls
devconnectpos/module-wishlist
devconnectpos/module-xretail
devconnectpos/module-xretail23
With this access, an attacker could have:
- Stolen credit card data by injecting payment skimmers into checkout code
- Created hidden backdoors for ongoing access to merchant systems
- Poisoned software updates so every store that updated got infected
- Delete all customers and demand a ransom
Sansec did not download any private repositories so we cannot tell whether any of the modules have been tampered with. Given that an attacker can easily hide their malicious injection, for example by spoofing a legitimate ConnectPOS employee, a full audit of the code bases is required to assert trustworthiness.
Why wasn't this detected?
GitHub has a secret scanning feature that automatically detects exposed credentials. This feature is enabled by default for public repositories but requires a paid plan for private repositories. Since ConnectPOS uses private repositories, we suspect they did not have this feature enabled.
Recommendations
The token is now revoked. That's the good news. The bad news? We don't know if anyone else found it during those four years. If you're running ConnectPOS, assume the worst and verify you're clean:
- Audit your installation: Review all ConnectPOS modules in your codebase for unexpected changes or suspicious code
- Compare against known-good versions: If you have backups from before September 2021, compare current files against those versions
- Run a malware scan: Use eComscan to detect any backdoors or malicious code
- Monitor for suspicious activity: Watch for unauthorized admin access or unusual checkout behavior
Timeline
| Date | Event |
|---|---|
| September 27, 2021 | Token added to ConnectPOS installation documentation |
| January 6, 2026 | Sansec reports the exposure to ConnectPOS |
| January 6, 2026 | ConnectPOS revokes the token |
| January 12, 2026 | Sansec publishes this advisory |
We commend ConnectPOS for their swift response in revoking the token within hours of our report. However, given the 4+ year exposure window, a thorough security audit of the affected repositories and downstream installations is warranted.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more

