Sansec analysis: 12% of online stores leak private backups

by Sansec Forensics Team
Published in Threat Research − February 07, 2023
Sansec discovered that one in nine online stores accidentally expose private backups. This mistake could have dire consequences. Online criminals are actively scanning for these backups, as they contain passwords and other sensitive information. Exposed secrets have been used to gain control of stores, extort merchants and intercept customer payments.

It is a common practice to make ad-hoc backups during store platform maintenance. The problem, however, is that these backups often end up in a public folder. Perhaps the administrator intended to remove it after the maintenance, but forgot about it? Few people would admit it, but these mistakes are extremely common, as Sansec research now shows. It is the first time a quantitative study reveals the large scope of this problem: more than 12% of stores risk getting hacked because of a small human error.

Sansec analysed online stores of various sizes (n=2037). On 250 stores, we found archives (such as ZIP, SQL, and TAR files) in the public web folder without access restrictions. These backups appear to contain database passwords, secret administrator URL, secret API keys, and full customer data (PII).
How can attackers find and abuse these backups?
How easy is it for an attacker to discover such backups? Unfortunately, easier than you may think. We have observed automated attacks against online stores, where thousands of possible backup names are tried over the course of multiple weeks. The attack includes clever permutations based on the site name and public DNS data, such as /db/staging-SITENAME.zip. Because these probes are very cheap to run and do not affect the target store performance, they can essentially go on forever until a backup has been found.
Sansec found multiple attack patterns from dozens of source IPs, suggesting that multiple actors are working to exploit this vulnerability.
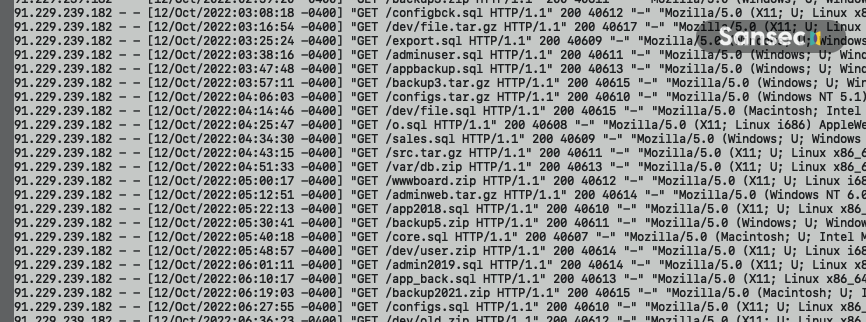
91.229.239.182And what if an attacker manages to download a private backup? They typically contain the secret administrator URL of a store, plus the password for the master database, plus hashed passwords for staff accounts. In many cases, these secrets are enough to gain administrator access.
Are you affected?
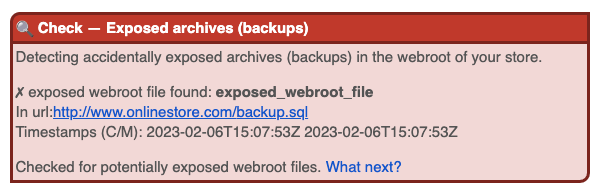
Hopefully not, but it cannot hurt to check your store for any backups in public folders. For any found files, test whether they are accessible via your public store URL. If your backups were accidentally exposed for a period of time, you should investigate your store for any signs of a compromise.
- Check your web server log files to see if your backup was downloaded.
- Check for any unauthorised admin accounts.
- Change all relevant passwords, notably admin accounts, SSH/FTP accounts, database passwords
- Ensure that all your staff uses two-factor authentication.
- Ensure that your site does not expose any remote database administration panels, such as phpMyAdmin or Adminer.
- Run an eCommerce malware scanner. Our backend security scanner eComscan was developed primarily to speed up this kind of investigations.
Preventing future leaks
Apart from not making ad-hoc backups at all, here are several effective strategies that will prevent future leaking of private backups.
- Deploy store code to a read-only filesystem so that no ad-hoc files can be made in the first place. Immutable storage is used by the hosted Adobe Commerce platform, which has several other benefits as well. If you are not on Adobe Commerce, implementing such a filesystem requires involvement from your hosting partner and isn’t always available.
- Schedule frequent backups so you do not have to make ad-hoc backup in the first place.
- Configure your web server to restrict access to archive files, such as ZIP, GZ, TGZ, TAR, and SQL. Of course, ensure that you don’t need to serve such files for legitimate reasons. Access restrictions can be added to htaccess files (Apache) or to the main Nginx configuration. Your hosting partner or DevOps team should be able to assist.
- Monitor for accidentally exposed files in the future, with an automated security scanner, like Sansec’s eComscan. Sansec has added alerting for this problem in the latest eComscan version.
Do you want to improve the security of your online store today for free? Get a copy of eComscan here and use the SECUREBACKUP coupon (first month free, no strings attached).
NB. Naturally, Sansec did not download any of the backups. We have reached out to merchants to verify our findings.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
