Bad extensions now main source of Magento hacks: a solution!

by Sansec Forensics Team
Published in Threat Research − January 29, 2019

In October last year I discovered several Magento extension 0days. As it turns out, this was only the tip of the iceberg: today, insecure 3rd party extensions are used to hack into thousands of stores. A group of Magento professionals have identified 63 vulnerable extensions, and are now releasing the Magento Vulnerability Database to help merchants counter these attacks.
Brief history of Magento hacks
The best part of our work as Magento forensic investigators is having front-row visibility into the craft of Magecart hackers. Over the last 4 years we have documented more than 40.000 breached Magento stores. The real figure is likely much higher, as not all hacks are visible from the outside.
In 2015, attackers used the "Shoplift" vulnerability in the core Magento code base. But as Magento upgraded their security policies, attackers shifted to brute force attacks on weak admin passwords during 2016 and 2017. Eventually, all the weak passwords got exhausted. And then in late 2018, a new attack method surfaced: exploiting insecure third party extensions. This quickly got traction, we estimate that several thousand stores were hacked this way in the last 3 months (we observed about 50 per day).
How extension attacks are spreading
The method is straightforward: attacker uses an extension bug to hack into a Magento store. Once in, they download all of the other installed extensions. The attacker then searches the downloaded code for 0day security issues, such as POI, SQLi and XSS flaws. Once found, the attacker launches a global scan to find vulnerable victims. Rinse and repeat.
Good protection, yet still getting hacked
The base of the problem is a conservative attitude among extension vendors. Contrary to Magento & Adobe, vendors generally fear loss of reputation and do not communicate about vulnerabilities. Those that do, may downplay the severity or bury it deep in their site.
Effectively, merchants are unaware of vulnerabilities in their installed extension base, which is typically 20 to 100 modules. Even though a successful merchant may have implemented all of the best practices:
- Use a dedicated Magento hosting provider with managed server/OS security.
- Have on-site dedicated Magento staff, or retain a specialized agency to perform timely (security) maintenance.
- Implement technical measures such as a third party WAF and other recommendations from the Magento Best Practices guide.
But they may still be running code with known vulnerabilities. As a safety net, these merchants could keep all of their extensions upgraded all the time but that is economically not feasible. Many extension releases are backwards incompatible, which requires costly developer hours. There is no standardized way to get notified of critical releases. And most important: merchants value stability above all, which does not fit well with a continuous upgrade policy. The fewer changes, the better.
We observe a sense of desperation among professional merchants, because they did all they could, and still got hacked.
Merchants: fear no more
A group of Magento professionals is proud to release a central repository of insecure Magento modules. It currently lists 63 insecure extension versions (and counting). Merchants can quickly run it against their store setups, find where they are at risk and selectively upgrade their extension base as needed:
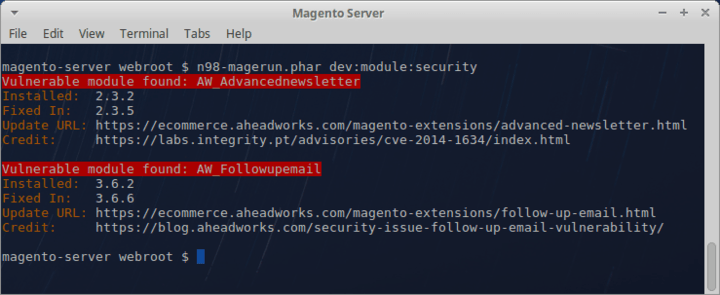
The Magento Vulnerability Database has been fully integrated with Sansec's eComscan security solution. Download a copy here.
Vendors & the future
We suspect that vendors will gradually move towards more transparent communication about security issues. Eventually, transparency will be a strong selling point for merchants who have suffered a breach in the past.
Until then, merchants should arm themselves with this data.
It is not our intention to shame vendors. We understand their position and risk calculations. However, we strongly believe we have to strive for transparency if we are to have a chance against this tsunami of extension attacks.
Acknowledgements
A big thank you to these Magento professionals who have contributed security research and code.
- Ryan Hoerr (contributed the n98-magerun plugin)
- Peter O'Callaghan
- Max Chadwick
- Jeroen Vermeulen
- Roland Walraven
- Martin Pachol
- Steve Perry
New contributions are welcome. Suspicious activity on your site? Do reach out, Sansec experts are ready to help you investigate.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
