Magento 1 still PCI compliant after 1 July 2020?

Magento 1 will no longer receive official updates & security fixes per July 1st, 2020 (the end-of-life, or EOL date). Merchants are urged to upgrade to Magento 2, but for many stores this deadline is not feasible. Merchants want to know:
- Will my Magento 1 store still be secure after July 1st?
- Will it still be PCI compliant, as required by my payment service provider?
Before we answer those, let's take a look at the numbers. Sansec actively monitors the global eCommerce space, and has observed a steady decline in Magento 1 stores. We estimate that 105 thousand Magento 1 stores will still operate beyond July 1st. Effectively, a great number of merchants need to prepare for the upcoming deadline.
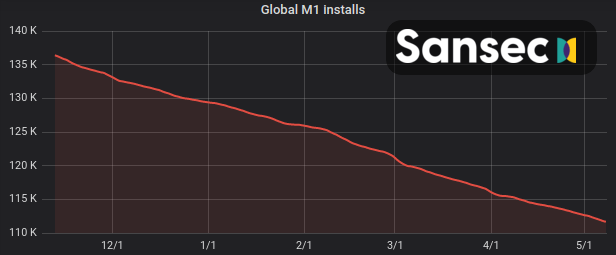
Will Magento 1 still be secure after July 1st?
Almost all hacked Magento stores are compromised via security bugs in the code. Therefore, the risk of getting hacked is a function of a) the discovery of new bugs and b) the ability to quickly patch those bugs.
Bugs can exist in core Magento code (as maintained by Adobe) and third party extensions.
Bugs in core Magento code
Bugs are discovered all the time. Since 2015, Magento has found and fixed hundreds of security bugs. But when they cease doing that, it surely would boost malicious actors? The reality is less frightening. Not all security bugs are equal. Out of hundreds of discovered bugs since 2015, only three bugs were super-bugs. They proved so critical that criminals could launch massive, automated hacks into stores. Many other bugs require specific conditions before they can be actually exploited. For example, criminals would need prior administrative access. Or exploitation requires weeks or months of sophisticated preparation. The chance of getting hacked via one of those minor bugs has proven to be negligible in practice.
However, there is a realistic chance that another super bug will be discovered in the coming months. You really should prepare for this event. First, make sure that you will receive a timely alert when a super bug is discovered. And second, you should have a plan ready so that you can apply a fix within 24 hours of discovery. Read ahead on how to accomplish this.
Bugs in 3rd party components
Another common source of Magento hacks are bugs in 3rd party components. Some vendors will release fixes, others will not. Key strategy here is getting timely alerts about vulnerable components, so you can take appropriate action. It is extremely costly to stay up to date on all your extensions, all the time. So selectively updating just those vulnerable extensions is a big cost saver.
Will Magento 1 be PCI compliant after July 1st?
Payment providers have released ambigious statements, which sparked extensive discussion. Merchants need to put proper safeguards in place, but what qualifies is up for interpretation. This has been discussed extensively, and Joe Rollinson has written an excellent overview. The gist of it: PCI requires you to install vendor security patches. If you cannot, you will need to implement compensating controls:
- Filtering common attacks is usually done by your hosting provider. If you are with a Magento-specialized hosting provider (see our partners), they will take care of that for you.
- Planning ahead will save you precious time, in the event that a security incident occurs. For medium to large merchants, an extensive response plan can be useful. All merchants, regardless of size, need to:
- Familiarize themselves with the possible channels for obtaining non-Adobe security fixes, such as via Mage-One and others
- Verify whether their backups are functioning correctly and whether server log files are properly kept (PCI requires 12 months retetion)
- Decide what technical capacity they can engage in an emergency situation and allocate resources.
- Scanning/monitoring creates visibility into possible risks and breaches, so that you can prevent or mitigate damage. Our eComscan monitor was developed specifically for this purpose. As it is the only specialized scanner for Magento, it will alert you to critical security bugs that generic scanners do not know about.
With these measures in place, you will be properly equipped to stay securely on Magento 1 beyond July 1st. And you will be able to present a convincing set of measures to apply for compensating controls with your payment provider, should it be necessary.
(M1 EOL image by Artūrs Krūze)
Read more
In this article
Protect your store now!
Block all known Magento attacks, while you schedule the latest critical patch until a convenient moment. No more downtime and instability from rushed patching.
Get Sansec ShieldScan your store now
for malware & vulnerabilities
eComscan is the most thorough security scanner for Magento, Adobe Commerce, Shopware, WooCommerce and many more.
Learn more

